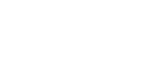Since China Data Security Law went live in September 2021, it has been almost 10 months. By looking back relevant cross-border data transfer regulations and industry practices, we wanted to summarize our observations and thoughts for multi-national companies who are keen on knowing a practical solution to achieve cross-border data transfer. We noticed that:
(1) More regulations are in progress on how to assess data security controls, and how to review and approve cross-border data transfer.
(2) Regulators are involving market participants from several sectors to conduct pilot studies on data security assessment and cross-border data transfer management.
We observed that regulators have been trying to sort out a practical solution for cross border data transfer. The progress, however, seems uneven across different sectors. Some industries show more activities in regulatory rule making than others do. Regulators are also faced with big challenges, especially the technical difficulties in defining important data scope and conducting data security assessment for cross-border data transfer. We summarized a compliance road map for multi-national companies and suggested our clients to closely monitor the progress and actively prepare for a safe and orderly cross border data transfer.
I. Background: Is It Possible to Transfer Data Cross Border?
One central theme of China Data Security Law (DSL) is to encourage data property usage via orderly and free data flowing while protecting individual and organizational legitimate interests in data (Article 7, DSL). Article 38 of China Personal Information Protection Law (PIPL) lists four separate conditions for personal information to be shared cross border. The first one is to pass security review organized by national cybersecurity authority[2]. Article 37 of China Cyberspace Security Law (CSL) specifies a similar condition of security review for Critical Information Infrastructure Operators (CIIOs) that intends to transfer personal information and important data abroad. In other situations of important data cross-border transfer, security review is also listed as a key requirement.
For most multi-national companies (MNCs) that are not qualified as CIIOs in China or not connected in certain ways to be considered same as CIIOs, they will be treated as other data processors. According to DSL Article 31, their important data cross-border transfer shall follow the security management rules made by CAC and sectoral regulators. Practical questions, however, remain open on what types of data possessed by market participants can be classified as important data for such security review, what are the contents of such cross-border security review, and, if personal information involved, what volume of personal information in scope will be considered for such governmental review.
For MNCs who are eager for answers to the above questions, at least two things are clear. Under the condition that cross-border data transfer does not violate any other laws or regulations[3],
(1) MNCs can legitimately share data cross border if such data are not classified as important data or personal information;
(2) For important data and personal information, MNCs can still transfer data across border if their data security control and transfer management can pass the government’s security review.
In this Study, we looked through relevant regulations, especially some new rules in specific areas, and regulatory activities to find out a compliance roadmap for MNCs to cross-border data transfer. For personal information, PIPL lists the conditions for cross-border transfer and specifies the privacy notice and the consent by data subject requirements. The main scope of this paper was limited to the general concept of data under China Data Security Law, not specifically focusing on personal information and its relevant security controls during cross-border transfer.
II. Regulatory Framework: Who Shall Approve Cross-Border Data Transfer?
According to DSL Article 5, the authority responsible for national data security matter is China central national security leading institution. Office of the Central Cyberspace Affairs Commission and its executive office Cyberspace Administration of China (CAC) are in charge of leading and coordinating all cyberspace related security matters. Under the central authority, DSL authorizes relevant responsible departments under the China State Council to supervise data security matters for the data generated from their respective sectors (Figure 1 Regulatory Framework for China Data Security Law Enforcement). Similarly for personal information and important data generated by CIIOs, Article 37 of CSL specifically requires CAC and relevant authorities to issue security review rules to govern cross-border data transfer. The Ministry of Public Security and the Ministry of National Security are responsible for public security and national security related data governance matters.
Figure1: Regulatory Framework for China Data Security Law Enforcement
In practice, it will be CAC and responsible departments or bureaus that are making sectoral specific data security rules, including official catalogs of important data and security assessment requirements for cross-border data transfer. They are the actual authority to conduct security review before such data transfer can be approved. For example, in 2021, CAC along with four other bodies including National Development and Reform Commission (NDRC), Ministries of Transportation, Industry and Telecom, and Public Security, issued the Regulation on Security Management of Automobile Data (for Trial Implementation) (Auto Data Regulation). Article 11 of this Regulation specifies a security review requirement for auto data cross-border transfer. The leading authority for such review will be CAC and the other ones who issued the Regulation.
III. A Compliance Roadmap: How Can Data Be Transferred Across Border?
By analyzing the requirements of DSL, CSL, and other relevant rules for cross-border data transfer, we identified a compliance roadmap for MNCs.
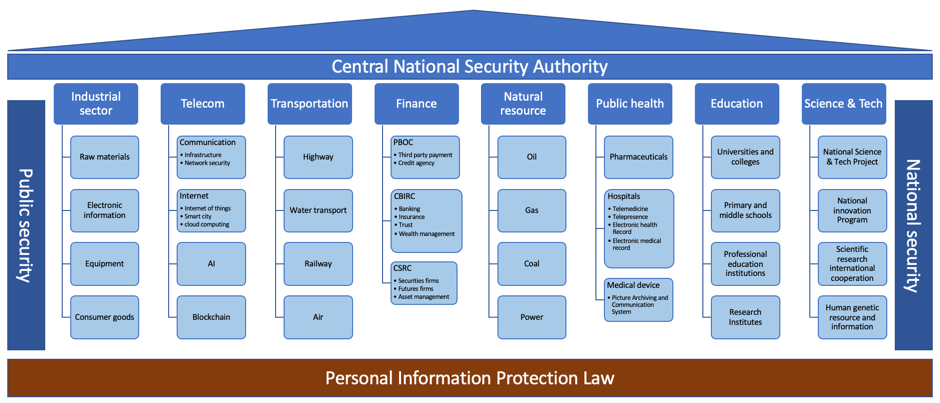
(1) Data Classification
The first critical step is to classify data based on their importance and impact if damaged (Figure 2 A Compliance Roadmap to Cross-border Data Transfer). Article 21 of DSL clearly specifies that relevant regulators shall issue formal catalogs of important data in their respective regions, sectors, or areas. The actual content of the catalogs, however, will be finalized through the interactions between regulators and the regulated industry. We observed several examples of market participants’ involvement in pilot studies and policy draft discussion organized by their sector regulators. One typical example is the Industrial Sector. Regulators are expecting that market participants can sort out their important data inventory and report their catalogs, by which processes the authority can develop a common practice for the sector and also law enforcement capacity.
Figure 2: A Compliance Roadmap to Cross-border Data Transfer
On January 13, 2022, China National Information Security Standardization Technical Committee released a consultation draft of Guidance for Identifying Important Data after multiple rounds of discussions among industry participants and relevant regulators. The drafting process also included a two-month pilot implementing test by some volunteering participants in the industrial sector[4]. In the draft, the standards for important data included two dimensions. One is the importance of data to social and economic development. Another is the potential impact on national security, public interest, individual or organizational legitimate interests if such data are tampered, damaged, leaked, illegally acquired or used. The operational level standards in each area within each sector will be further interpreted by responsible regulators.
Auto Data Regulation in automobile industry sets up a good example for this practice. Para 6 of Article 3 in the Regulation lists six types of important data in auto field:
(i) Data of important sensitive areas including military administrative zones, national defense science and technology departments, and communist party and government offices at the county level or above; data types include geographical information, passenger flow, automobile flow and others;
(ii) Economy operation data reflected by automobile flow, logistics and other similar data;
(iii) Automobile charging network operation data;
(iv) Automobile external video and image data that include human facial information and car plate information, etc.;
(v) Personal information involving more than 100,000 individual personal information subjects;
(vi) Other data determined by authority that can be relevant to national security, public interests, individual or organizational legitimate interests.
The above scope of automobile important data shows that the standards of important data are often related to macro level information reflecting national or regional economy, sensitive geographic information, or large volume of personal information for individuals. Except for personal sensitive information reasons, MNCs’ business data with only small amount of data subjects may not be qualified as important data.
With a full inventory of important data and other types of data, MNCs can file with authority such information for regulatory review and assessment purposes. It also serves a good starting point for MNCs to initiate discussion with regulators.
MNCs should pay attention to any special data localization requirements by the current sectoral laws or regulations. Some of them are for national security or public interest protection purposes. Other policies may be based on factors that can be re-considered under the new DSL protection regime. While regulators are making new implementation rules for DSL, there could be rooms for further revisions.
(2) Data Security Protection Management
MNCs, often as data processors, have obligations to protect data and implement their own data security management through daily operation. As part of internal controls, MNCs can form a separate compliance process for data security management or integrate the process with their existing overall compliance program. For important data transferred cross border by data processors other than CIIOs, Article 31 of DSL specifies that CAC will issue specific cross-border transfer security management rules along with responsible sectoral regulators.
With regulatory guidance and internal implementation, MNCs shall be ready to file their internal control policies and procedures with regulators, to file report for each data security incident and its remediation, to conduct risk assessment periodically, and to file the assessment reports, normally on annual basis.
On the enforcement side, DSL requires government to build up data security protection, risk assessing, reporting, information sharing, risk monitoring and alert warning processes. A challenging task for all regulators is to develop special expertise and enforcement capacity in those areas. MNCs may have their strengths and international experience in data security protection, which will be much valued by Chinese regulators. MNCs should leverage the expertise and actively interact with regulators during the rule making processes.
(3) Important Data Risk Assessment
With important data catalog issued by regulators, MNCs shall conduct periodical risk assessment for their data management activities and file reports with their respective regulators. The reports shall include the types of important data MNCs process, the scope and amount of important data, the activities of data processing, potential data security risks and their respective control measures. (DSL Art. 30)
(4) Cross-border Data Transfer Security Assessment
The example of Auto Data Regulation shows that MNCs can most probably be required to conduct additional risk assessment for cross-border data transfer. According to Article 14 of Auto Data Regulation, besides normal data security management assessment items, the assessment for cross-border activities will also need to include the following items:
(i) Offshore data recipient information;
(ii) Cross-border data types, amount, purpose and necessity;
(iii) Offshore data depository location, term, scope and method of data saving;
(iv) Consumer complaints and handlings related to cross-border transfer;
(v) Other information required by authority.
The results of such special assessment are also required to be filed with regulators. For important data, the relevant authority shall conduct security assessment and review before such data can be allowed to transfer.
(5) Cross-border Data Transfer Practice and Regulatory Supervision
After MNCs are allowed to transfer data cross border, MNCs shall maintain security management over the transfer process and keep all the relevant records. Regulators can conduct inspections by sample checking such data transfer or by a full range examination.
Other regulatory reviews may also be from the perspectives of cyberspace security for CIIOs or personal information protection under PIPL.
The compliance roadmap of Figure 2 lists the five key steps for cross-border data transfer. Each step also represents one major task for government to formalize specific implementation rules in each area. The responsibility falls on the shoulders of CAC and regulators in each sector. The actual enforcement will depend on how those regulators frame and interpret the rules.
IV. Cross-Sector Analysis of Regulatory Rules: Open Questions and What’s the Next?
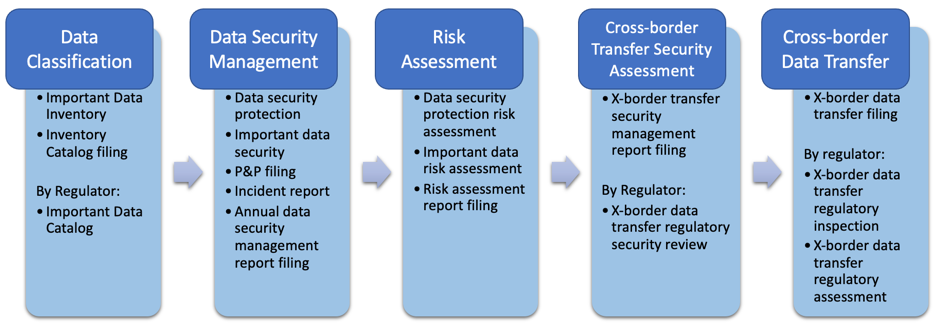
We conducted a comparison analysis of the developments in data security regulations across different sectors in China. We reviewed the major regulatory rules within each sector under China State Council to summarize the status of each key step within the roadmap. In most fields, we are still waiting for formal rules to implement the new DSL in each sector (Table 1). We observed different progresses across sectors and remarkable developments in some special areas such as automobile data. In some sectors, there are pilot studies organized by regulators to collect feedback from market during the rule making process. In some areas, for example, human genetic resource and information, formal regulations on cross-border activities exist even before DSL. The darkness of green fields in Table 1 under the key steps of the roadmap reflects the intensity of regulatory activities we observed. The darker the green fields are, the more regulatory activities we noticed.
Table 1: Cross-Border Data Transfer Regulation and Pilot Studies
(1) Existing Regulations
In some sectors, along with recent Cyberspace Security Law and relevant regulations, regulators have been active in supervising data security matters. The regulatory focuses, however, are often on one or two of the key steps under the roadmap. Data classification is the most common area across sectors. We identified data classification rules for industrial sector data[5], basic telecommunication data[6], cyberspace data[7], financial data in finance[8] and, more specifically, connected vehicle data, securities and futures data[9] in the sector of finance. On data security assessment, there is one implementation guidance for telecommunication network and Internet[10].
Other existing rules are at a broader level covering multiple steps in the methodology but only applicable to limited areas. For examples, on internet information service algorithmic recommendation governance[11] and health data governance[12], there are special data security management rules issued in the last two years.
A special area under tight supervision is human genetic resource and information, which is commonly relevant to life science and medical sectors. Even before DSL, the Chinese government has formalized a regulation to manage the collection, use, transportation and information sharing of human genetic resource and information[13]. For the purpose of scientific research international cooperation, human genetic resource can be provided with offshore if such activities can meet the required conditions and are approved by the regulator in the Ministry of Science and Technology. If human genetic information sharing can have impact on public health, national security and social public interest, the regulator shall conduct security review before it can approve such sharing.
The compliance roadmap summarizes the DSL methodology of managing data security across sectors. We expect more implementing rules will come up on cross-border data transfer. The rules on automobile data[14] and internet of vehicle network[15] are the live examples even though operational level practices are still in pilot testing stage.
(2) Regulations in Progress and Pilot Studies
More rules under discussion focus on the matter of security assessment for transferring data cross border in general[16] and for personal information and important data[17] specifically. On important data identification and classification, there are also ongoing efforts in regulatory guidance drafting either in general[18] or for a specific sector, for example, the industrial sector[19].
In the industrial sector, especially in automobile related industry, we observed intensive rule making activities on data security management[20]. More importantly, the regulators in this sector have kicked off a series of pilot studies on data security management with market participants. The initiative includes cross-border data transfer trial projects in the provinces of Zhejiang and Hainan. The regulators targeted to complete the pilot project around September 2022. The aim is to get the industry involved and to develop more practical rules. The auto industry and relevant third-party security assessment institutions are actively participating in the project.
In other government’s endeavors to internationalize its economy, we also noticed other pilot studies. For example, in Macau and Hengqin Cooperation Zone, there is a pilot initiative to develop free and safe data sharing between internet and local networks and to carry out cross-border scientific and research data transfer among universities and colleges between Macau and the city of Zhuhai[21].
(3) Other Areas with Governmental Strategic Plans
Chinese government has pushed for an overall digitalization of China economy and social governance. We’ve observed multiple strategic planning activities across sectors with attentions to data security and risk management. They include Uber-type taxi service and cargo transportation management, foreign-China joint exploration of natural resource, energy management and other topics. We expect those plans will further grow into pilot studies on data security management and cross-border data transfer management.
On the regulated side, we also noticed self-driven efforts by industry associations in pharmaceutics[22], financial industry[23], and credit agency[24] to form common data compliance practices and to advocate for cross-border data transfer.
V. Conclusion: What Should We Do to Prepare?
We noticed similar endeavors by regulators across sectors to sort out a practical solution to cross-border data transfer. The regulators, however, face challenges, especially the technical difficulties in defining important data scope and conducting data security assessment for cross-border data transfer. The finalization process of relevant regulatory rules will take more time. MNCs need to be more patient than expected to have a clear guidance and then to form a practical compliance solution.
Our observations suggested that the rule making is not going to be a from-top-to-down approach. The close cooperation between market participants and their regulators becomes a practical way that works for both sides and better serves for both compliance and efficiency purposes. Therefore, we expect more participation from market players in this area. We suggest that MNCs maintain a positive attitude toward “regulatory guidance” and actively voice out their own agenda and priorities during the process.
(1) To Start Data Classification and to Localize Data Governance Mechanism
Data classification and security protection are the basic components of China data security regulation. Such topics and related governance processes will definitely be included in the security assessment and reviews by the authorities. Even though we are still waiting for more detailed guidance, we suggest international firms start field work to sort out their own data inventory and specify data security controls. More specifically for foreign firms with an existing global data governance framework, we suggest MNCs start planning for a localized version with a properly pre-defined scope of data and verifiable processes of controls. Their senior management teams shall think over the company overall data strategy and adapt it to the local context in order to accommodate their business development plan in China.
The roadmap is becoming clear. It will be MNCs’ own task to implement the rule-based compliance framework.
(2) To Strategically Plan Data Security Investment in China
International firms have been proud of their own globalized management and operational platforms. Chinese regulators are always interested in learning such international experience. But they also want to see a real governance process that they can understand and supervise. MNCs should plan investment to localize their data governance mechanisms. Even without definitive answers to some of the key questions, we are clear that important data and personal data shall be stored locally and sufficient security controls should be in place.
With such investment in mind, MNCs should start strategic planning as early as possible to think through their data classification, management and data application processes, especially for those types of data that will not be possibly allowed to freely flow cross border. The plan should also include a strategy for communicating with regulators, including making data and their control interfaces more accessible and user-friendly to regulators. In the new era of Big Data, it is a cost for doing business that no one can avoid.
(3) To Actively Advocate for Free Data Sharing and Usage
Free and orderly data movement is a critical element for data to become one type of asset and production factor. DSL and other China data policies have endorsed this element while emphasizing data security. Article 11 of DSL highlights that China is actively participating in international communication and cooperation on data security governance, data development, and data usage. China is actively participating in data security related international rule and standard making, and willing to encourage safe and free data transfer across border.
US-China relationship and geo-politics are becoming complex during the current environment. We remind ourselves and all our clients to carefully navigate through the complex environment and to leverage all factors favorable to our business. For areas temporarily without clear rules, we suggest MNCs actively advocate for rules with preferences for free data sharing and usage. Industrial associations or self-regulated organizations can help on such advocacy effort.
For data not as important as the ones relevant to national security and economic security, MNCs can put on more effort for advocacy. It is a process of negotiation. We also suggest MNCs prepare interim solutions for those data matters that are pending official guidance. The solutions should be defended with sufficient justification and robust security protection.
(4) To Closely Monitor Regulatory Trends and Actively Participate in Pilot Studies
Market participants shall closely monitor the development of data policies. One way is to track pilot studies organized by regulators and to pay close attention to the best practices survived from the tests. Periodical peer benchmarking is also a valuable practice for MNCs.
We recommend MNCs actively seek for opportunities to participate in pilot studies or similar channels to interact with regulators and peer firms.
Notes:
[1] Special thanks to Hanqing Wei for her legal research assistance.
[2] Under each of the other three conditions, personal information can also be shared cross border per Art. 38, PIPL.
[3] The other laws and regulations include China Law on Guarding State Secrets, or other special laws or regulations that require data to be localized in China.
[4] On Jan 13, 2022, National Information Security Standardization Technical Committee released a consultation version of Guidance for Identifying Important Data. See https://www.tc260.org.cn/front/bzzqyjDetail.html?id=20220113195354&norm_id=20201104200036&recode_id=45625
[5] Guidelines for Industrial Data Classification and Grading (Trial) (《工业数据分类分级指南(试行)》).
[6] Data Classification and Grading Method of Basic Telecommunication Enterprises (《基础电信企业数据分类分级方法》) and Important Data Identification Guide for Basic Telecommunication Enterprises (《基础电信企业重要数据识别指南》),
[7] Practice Guide for Cyberspace Security Standards – Guidelines for Classification of Cyberspace Data(《网络安全标准实践指南——网络数据分类分级指引》).
[8] Financial Data Security – Guidelines for Data Security Classification (《金融数据安全 数据安全分级指南》).
[9] Data Classification Guidelines for Securities and Futures Industry (《证券期货业数据分类分级指引》).
[10] Data Security Risk Assessment Implementation Guide for Telecommunication Network and Internet (《电信网和互联网数据安全风险评估实施方法》).
[11] Internet Information Service Algorithm Recommendation Management Rules (《互联网信息服务算法推荐管理规定》).
[12] Information Security Technology - Guide for Health Data Security (《信息安全技术 健康医疗数据安全指南》) and Big Data Standard, Security and Service Management Rules for National Health and Medical Industry (《国家健康医疗大数据标准、安全和服务管理办法》).
[13] Human Genetic Resource Management Interim Rules (《人类遗传资源管理暂行办法》) and Human Genetic Resource Regulation (《人类遗传资源管理条例》).
[14] Automobile Data Security Management Regulation (Trial Implementation) (《汽车数据安全管理若干规定(试行)》).
[15] Standard System Construction Guideline for Internet of Vehicle Network Security and Data Security (《车联网网络安全和数据安全标准体系建设指南》).
[16] Measures for Security Assessment for Cross-border Data Transfer (Draft for Comment) (《数据出境安全评估办法(征求意见稿)》) and Information Security Technology – Guidelines for Data Cross-Border Transfer Security Assessment (Draft for Comment) (《信息安全技术 数据出境安全评估指南(征求意见稿)》).
[17] Measures for Security Assessment for Cross-Border Transfer of Personal Information (Draft for Comment)《个人信息出境安全评估办法(征求意见稿)》 ; Measures for Security Assessment for Cross-Border Transfer of Personal Information and Important Data (Draft for Comment) (《个人信息和重要数据出境安全评估办法(征求意见稿)》).
[18] Information Security Technology – Guidelines for Important Data Identification (Draft for Comment) (《信息安全技术 重要数据识别指南(征求意见稿)》).
[19] Administrative Measures for Data Security in the Fields of Industry and Information Technology (Trial) (Draft for Comment) (《工业和信息化领域数据安全管理办法(试行)(征求意见稿)》 ).
[20] Data Security Assessment Guidelines for Intelligent Connected Vehicles (Draft for Comment) (《智能网联汽车数据安全评估指南(征求意见稿)》) and Administrative Measures for Data Security in the Fields of Industry and Information Technology (Trial) (Draft for Comment) (《工业和信息化领域数据安全管理办法(试行)(征求意见稿)》).
[21] Hengqin Yue Macau Deep Cooperation Zone Construction General Plan (《横琴粤澳深度合作区建设总体方案》). See http://www.gov.cn/zhengce/2021-09/05/content_5635547.htm.
[22] For example, China Association of Enterprises with Foreign Investment, R&D-based Pharmaceutical Association Committee (RDPAC).
[23] Global Financial Markets Association (GFMA), 2019, GFMA Comments to Cyberspace Administration of China on Measures on Data Security, https://www.gfma.org/wp-content/uploads/2019/06/gfma-response-consultation-measures-on-data-security.pdf .
[24] Professional Committee of Credit Management (PCCM), Nov 23, 2021, Forum on Enterprise Credit Data Cross-border Transfer. http://www.pccm-credit.com/?p=1699 .