With the rapid development of information technology, the security of personal information becomes more and more important in the era of Big Data. In recent years, laws and regulations in different jurisdictions have established personal data protection regimes in accordance with their specific contexts, all of which contain provisions relating to personal information breaches.
The General Data Protection Regulation (“GDPR”) of the European Union (“EU”), which was described as “the toughest ever”, took effect in May 2018. In contrast to EU, the legislation protecting personal information at the federal level in the United States will be found in many different pieces of laws and regulations[1]. At the state level, the California Consumer Privacy Act of 2018 (“CCPA”) is one of the landmark acts to protect consumer’s personal data in the United States.[2] The People’s Republic of China (“PRC”) issued the Personal Information Protection Law (“PIPL”), which came into force on November 1, 2021, making it the first statute to specifically regulate the protection of personal information in PRC.
A basic framework of the personal information protection generally includes (a) defining the personal information to be protected, (b) specifying the rules to be complied by “data processors” when handling personal information and the rights of protected subjects, (c) setting up legal procedures and requirements for the breach and cross-border transfer of personal information, and (d) establishing relevant penalties, etc. One of the major concerns of many enterprises is then whether they are subject to notification obligations after the occurrence of a personal information breach event, in addition to their obligations to take other remedial measures. In this article, we will compare the enterprises’ notification obligations regarding the occurrence of personal information breach events from the perspectives of PIPL, GDPR and CCPA, respectively, as a guidance for enterprises to better understand the compliance requirements of personal data protection.
Before discussions in detail, we prepared the following table to compare the aforementioned three jurisdictions, in legislation areas of the obligors and their definitions, protected information/data, protected subjects, notification obligations, notified parties and supervisory authorities:

Part I: Personal Information Processer/Data Controller shall comply with the notification obligation regarding personal data breach
1. Whether the leaked information is personal information?
In the event of the breach of a personal information/personal data (collectively “personal information”), an enterprise (as the personal information processor/data controller) ought to first check whether the information leaked in such event is personal information as defined by laws. The following table compares the definitions of personal information in different statutes:
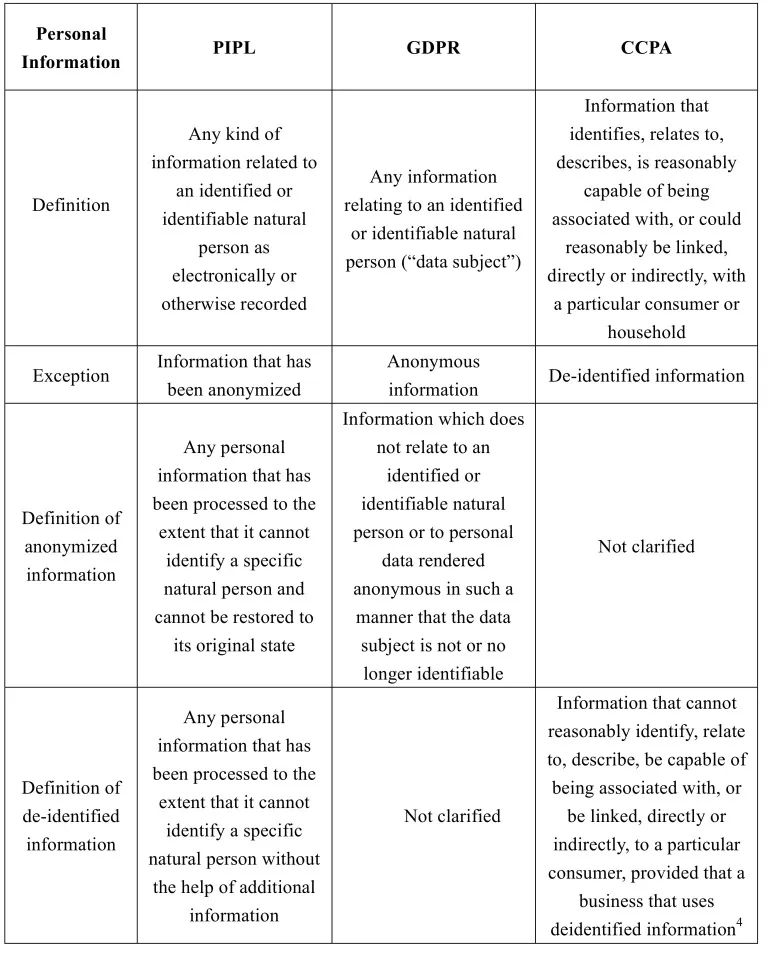
Both PIPL and GDPR emphasize identified or identifiable natural persons in the definitions of personal information. GDPR explains identifiable natural persons by example, i.e., an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as name, identification number, location data, online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person[5].
PIPL however does not specifically define identifiable natural persons and their related details. Article 1034 of the Civil Code of PRC lists different types of personal information to be protected, such as the name, date of birth, identification number, biometric information, residential address, telephone number, email address, health information, and location data of the natural person[6], etc. In addition, PRC has adopted a recommended national standard that describes personal information by example[7].
Comparatively speaking, CCPA has a broader definition of personal information than PIPL and GDPR, but lists certain representative categories of personal information[8] and including family, identity-related and device information as personal information.
Also, as shown in the table above, both PIPL and GDPR indicate that the protection of personal information does not apply to anonymized information[9]. While CCPA does not explicitly adopt the concept of “anonymization”, it applies the concept of de-identification, i.e., CCPA does not restrict enterprises from collecting, using, retaining, selling or disclosing de-identified or aggregated consumer information. PIPL borrows this concept of de-identification and defines “de-identified” as in the table above. Nevertheless, PIPL does not exclude “de-identified” personal information from its scope of protection.
In addition, CCPA clearly defines that personal information shall not include: (a) publicly available information; (b) lawfully obtained, truthful information that is a matter of public concern; and (c) aggregated information. Such exceptions are however not reflected under PIPL.
In summary, when determining whether the leaked personal information is personal information protected under the PRC legal system, enterprises should consider the definitions of personal information under PRC laws and analyze this issue in the context of the specific circumstances of the breach event.
2. How to define personal information breach?
In GDPR, “personal data breach” means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed[10].
Unlike GPDR, CCPA does not provide a clear definition of personal information breach. Comparatively speaking, California Civil Code defines “security breach” as unauthorized acquisition of computerized data that compromises the security, confidentiality, or integrity of personal information, excluding certain good faith acquisitions.[11]
There is no direct definition of personal information breach in PIPL. PIPL only stipulates that in the event or possible event of personal information leakage, falsification, and loss, personal information processors should conduct their corresponding notification actions.
3. What are the notification obligations regarding personal information breach events?
GDPR requires the controller to notify both supervisory authorities and data subjects in case of a personal information breach event. Under GDPR, the controller shall without undue delay notify the personal information breach to the supervisory authorities, unless the personal information breach is unlikely to result in a risk to the rights and freedoms of natural persons[12]. When the personal information breach is likely to result in a high risk to the rights and freedoms of natural persons, the controller must further communicate the personal information breach to the data subject without undue delay[13].
Similar to those in GDPR, the provisions governing the notification obligations regarding personal information breach event in PIPL stipulate that in the event of personal information leakage, falsification and loss, personal information processors should immediately take remedial measures and notify the authorities-in-charge and the individuals concerned. In addition, PIPL also sets out the circumstances under which personal information processors are exempted from notification obligations owed to the individuals concerned, which will be specifically discussed under Part II / Section 1 of this article.
On the other hand, CCPA only stipulates that “businesses” should notify consumers of specific matters before collecting personal information, and does not specify any notification obligations after the occurrence of any personal information breach event. However, supervisory authorities or individuals may leverage breach notification obligations that exist under the general breach notification provisions under the California Civil Code to require all agencies, businesses, and persons that conduct business in California to conduct their notification obligations in the event of personal information breach[14].
4. How to determine whether the enterprise is an entity subject to such notification obligations?
As discussed above, CCPA does not specify the entity to fulfill notification obligations after a personal information breach event. Based on the provisions regarding general breach notification obligations under California Civil Code, we may infer that “businesses” defined in CCPA shall be one of the entities to fulfill such notification obligations.
Under GDPR, the controller is the entity that performs the notification obligations upon a personal information breach event. The controller in GDPR is defined as the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data[15].
Under the PIPL, the personal information processor is the entity that performs the notification obligations. The definition of “personal information processor” in PIPL is similar to “controller” under GDPR, both of which emphasize the independent decision-making power of such entities on the processing of personal information. As mentioned above, the personal information processor refers to any individual or organization that independently determines the purpose and method of processing in their activities of personal information processing. It should be noted that PIPL also stipulates that personal information processors who jointly process personal information shall be jointly and severally liable for any infringement of personal rights and interests in their joint processing of personal information[16]. Accordingly, we understand that personal information processors jointly involved in the processing of personal information should also perform the corresponding notification obligations if any risk of personal information breach occurs.
Part II: Enterprises shall assess how to perform their notification obligations according to the specific circumstances of personal information breach events
1. The severity of personal information breach events determines how to perform notification obligations
Under GDPR, data controllers are not required to comply with their notification obligations to supervisory authorities if such personal information breaches are unlikely to result in a risk to the rights and freedoms of natural persons[17]. When the personal information breach is likely to result in a high risk to the rights and freedoms of natural persons, the controller need to communicate the personal information breach to the data subject without undue delay. Meanwhile, data controllers may be exempted from their notification obligations to data subjects if they meet certain criteria stipulated in GDPR[18]. In addition, considering the risk of a personal information breach, the supervisory authorities may ex officio require data controllers to perform their notification obligations to data subjects according to GDPR[19].
Similar to GDPR, PIPL entitles the personal information processor not to notify the individual concerned if the personal information processor can take measures to effectively avoid the damage caused by the leakage, falsification, or loss of information[20]. However, the supervisory authorities may require the personal information processor to notify the individual if they believe it may cause harm to the individual. Unlike GDPR, PIPL does not specify the circumstances under which the notification obligations to supervisory authorities are exempted.
Although PIPL does not impose individual notification requirements for every personal information breach event, PIPL does not set forth specific criteria for personal information processors to determine whether the damage caused by the breach “can be avoided”. Besides, there are no exceptions to the obligations of personal information processors to notify supervisory authorities. Probably due to the recent effectiveness of PIPL, PRC supervisory authorities have not provided a detailed interpretation of this provision, which remains to be clarified by future legislation.
2. The content of notification required to contain certain specific information, and specific time limit imposed to notify supervisory authorities
GPDR includes the detailed content requirements of the data controller’s notification and the time limit for such notification obligations to the supervisory authorities under personal information breach events. However, GPDR does not specify a time limit for data controllers to perform their notification obligations to data subjects (it only points out that such notification should not be unreasonably delayed). Similar to GDPR, PIPL also specifies the notification content when personal information processors perform their notification obligations[21]. Nevertheless, PIPL does not specify time limits for personal information processors to perform their notification obligations, neither to the supervisory authorities or to the individuals concerned. We also listed the required notification contents and time limits for businesses to conduct their notification obligations under California Civil Code.
The following table compares time limits for the notification obligations and notification content requirements under PIPL, California Civil Code and GDPR:
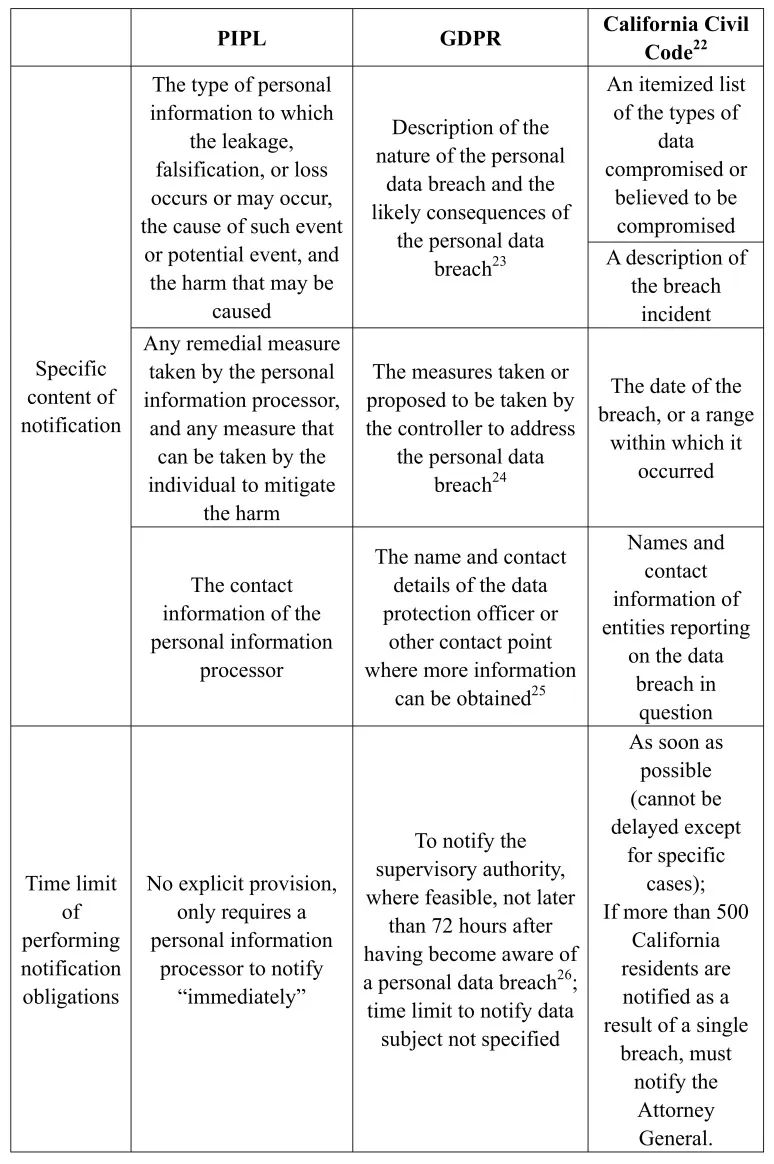
We noted that, other than the aforementioned provisions, PIPL and other PRC effective laws and regulations do not include clear interpretations on issues such as the “threshold” for triggering notification obligations, the specific department and level of supervisory authorities to which personal information processors shall notify, etc.
PRC is now gradually building its personal information protection legal regime, including further fine-tuning provisions relating to personal information processor’s performance of their notification obligations. The Cyberspace Administration of China released the Regulations on Network Data Security Management (Draft for Comment) on November 14, 2021, which states that if a data security breach event occurs, the data processor shall notify any interested party within three business days. In the event of a data security breach event such as the leakage, falsification, loss of Important Data or personal information of more than 100,000 people, the data processor shall report the basic information of the event to the city-level cybersecurity authority and other relevant competent authorities within eight hours of such event, and submit an investigation and assessment report to the city-level cybersecurity authority and other relevant competent authorities within five days after the event is completely handled[27]. Although the above regulations are still for public comment, they have reflected the attitude from the regulators on this aspect. We expect that the formal implementation of relevant laws will help enterprises, as personal information processors, to better establish their internal personal information protection compliance systems.
3. Foreign enterprises might also be subject to the notification obligations under PIPL
In addition to their domestic/territorial jurisdiction on processing of personal information, personal information protection laws in different jurisdictions also differ on their scopes of governed jurisdictions. The jurisdiction principle of GDPR embodies “territory + nationality”[28], i.e., GDPR being able to govern the processing of personal information of data subjects within the territory of EU by foreign entities located outside EU. CCPA and California Civil Code, as California state codes, their jurisdictions follow the “territory” principle and only govern commercial activities conducted within the State of California.
Unlike GDPR and CCPA, the jurisdiction principle of PIPL embodies “territory + exceptions”, i.e., PIPL having jurisdiction over foreign enterprises (entities not located in the territory of PRC) under certain “exceptional” provisions. These exceptions include: the purpose of the activity is to provide a product or service to natural persons located within PRC, the purpose of the activity is to analyze or assess the behavior of natural persons located within PRC, and other circumstances as provided by law or administrative regulations[29].
For foreign enterprises not conducting business through entities established in PRC, they should also comply with those notification obligations under PIPL under such “exceptional” provisions. According to the requirements of PIPL, such foreign enterprises shall establish a special agent or appoint a representative within the territory of the PRC to be responsible for personal information protection-related matters, and submit the name of such agent or the name and contact information of the representative to the supervisory authorities[30]. Nevertheless, the specific department and level of supervisory authorities to which the personal information processor shall notify and the process of such notifications are still subject to further clarifications.
4. Penalties for breach of the notification obligations
According to GDPR, in addition to being subject to the relevant orders made ex officio by the supervisory authorities[31], if an enterprise breaches its notification obligations, it may be subject to a fine up to EUR 10 million, or up to 2 % of its total worldwide annual turnover of the preceding financial year, whichever is higher; if a material breach of the notification obligations occurs, such as the non-compliance with an order by the supervisory authorities, it may be subject to a fine up to EUR 20 million, or up to 4 % of its total worldwide annual turnover of the preceding financial year, whichever is higher.[32]
The penalties imposed to enterprises for violations of notification obligations under PIPL are different. According to PIPL, in addition to imposing fines on the violating enterprise, the supervisory authorities may further impose fines on the person in charge or any other individual directly liable for such violation (the “Responsible Person of the Enterprise”), and may also impose other administrative penalties on both the enterprise and its Responsible Person of the Enterprise.
According to Article 66 of PIPL, any enterprise that violates the notification obligation may be subject to a fine up to RMB 1 million. If the violation is serious, the fine could be up to RMB 50 million or up to 5% of its turnover of the preceding year. For the Responsible Person of the Enterprise, he/she may also be subject to a fine between RMB 10,000 and RMB 100,000, or between RMB 100,000 and RMB 1 million if the circumstances are serious.
In addition, according to the seriousness of the circumstances, a personal information processor who fails to fulfill the notification obligation regarding personal information breach may be subject to orders to make corrections, warnings, confiscation of illegal gains, orders to suspend related activities or to suspend business for rectification, revocation of relevant business permits or business licenses, etc. The Responsible Person of the Enterprise may be banned for a certain period of time from serving as a director, supervisor, senior officer or personal information protection officer of a relevant enterprise.
Part III: Conclusion
Since major global economies are developing their own personal information protection legal regimes, multinational corporations are recommended to establish their internal compliance systems for personal information protection in different jurisdictions as early as possible. PRC’s personal information legal system is also gradually evolving. With an established compliance system, when there is a risk of personal information breach, enterprises may utilize their established step plans to determine whether they have any statutory notification obligations, and to perform their notification obligations in accordance with statutory requirements.
Notes:
[1] On June 3, 2022, a bipartisan draft of a federal data privacy bill, known as the American Data Privacy and Protection Act (ADPPA) is released. The ADPPA is a draft act proposing a strong federal regime for personal data protection in the US.
[2] In 2020, California passed the California Privacy Rights Act (CPRA). The CPRA amends certain parts of CCPA. Meanwhile, general data breach notification obligations of businesses are also stipulated in California Civil Code.
[3] “Consumer” means a natural person who is a California resident, which is defined in Section 17014 of Title 18 of the California Code of Regulations as (1) every individual who is in the State for other than a temporary or transitory purpose, and (2) every individual who is domiciled in the State who is outside the State for a temporary or transitory purpose.
[4] Cal. Civ. Code §§ 1798.140(h)
[5] GDPR Article 4 (1)
[6] Civil Code of PRC, Article 1034: A natural person’s personal information is protected by law. Personal information is the information recorded electronically or in other ways that can be used, by itself or in combination with other information, to identify a natural person, including the name, date of birth, identification number, biometric information, residential address, telephone number, email address, health information, whereabouts, and the like, of the person.
[7] GB/T 35273-2020, Information Security Technology-Personal Information Security Specifications, 3(1)
[8] Cal. Civ. Code §§ 1798.140(o)
[9] PIPL Article 4, GDPR Recital 26
[10] GDPR Article 4(12)
[11] Cal. Civ. Code §§ 1798.82 (g)
[12] GDPR Article 33(1)
[13] GDPR Article 34(1)
[14] Cal. Civ. Code §§ 1798.29, Cal. Civ. Code §§ 1798.82
[15] GDPR Article 4(7)
[16] PIPL Article 20
[17] GDPR Article 34(1)
[18] GDPR Article 34(3): (a) the controller has implemented appropriate technical and organisational protection measures; (b) the controller has taken subsequent measures which ensure that the high risk to the rights and freedoms of data subjects is no longer likely to materialise; (c) it would involve disproportionate effort
[19] GDPR Article 34(4)
[20] PIPL Article 57
[21] PIPL Article 57
[22] Cal. Civ. Code §§ 1798.82 (d)
[23] GDPR Article 33 (3) (a): describe the nature of the personal data breach including where possible, the categories and approximate number of data subjects concerned and the categories and approximate number of personal data records concerned; GDPR Article 33 (3) (c)
[24] GDPR Article 33 (3) (d): describe the measures taken or proposed to be taken by the controller to address the personal data breach, including, where appropriate, measures to mitigate its possible adverse effects
[25] GDPR Article 33 (3) (b)
[26] GDPR Article 33 (1)
[27] The Regulations on Network Data Security Management (Draft for Comment) Article 11
[28] GDPR Article 2, Article 3
[29] PIPL Article 3(2)
[30] PIPL Article 53
[31] GDPR Article 58
[32] GDPR Article 83 (4), Article 83 (5), Article 83 (6)
-
 业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Outbound Investment、Compliance & Risk Control、Life Science & Healthcare
业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Outbound Investment、Compliance & Risk Control、Life Science & Healthcare -
 业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Life Science & Healthcare、Compliance & Risk Control、Environment, Social & Governance (ESG)、Digital Economy and Data Security
业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Life Science & Healthcare、Compliance & Risk Control、Environment, Social & Governance (ESG)、Digital Economy and Data Security








