In recent years, countries around the world are strengthening the supervision on personal information and data protection. Taking the General Data Protection Regulation of the European Union (“GDPR”) as an example, one of the key supervision focuses is the cross-border transfer of personal data. The People’s Republic of China (“China” or “PRC”) has also been gradually implementing its legislation of personal information and data cross-border transfer regulations in recent years. In this article, we try to analyze the regime of cross-border transfer of personal information and data by comparing the relevant provisions under GDPR and PRC laws, aiming to provide references for enterprises to establish their compliance protocols for cross-border transfer of personal information and data.
I. General Framework of the Regulations of Cross-border Transfer of Personal Information and Data
GDPR includes detailed provisions on cross-border transfer of personal data in Chapter V, “Transfers of personal data to third countries or international organisations”, including provisions regarding Adequacy Decision, Appropriate Safeguards, Derogations for Specific Situations etc. We will discuss the details of these provisions in the “Requirements on Cross-Border Transfer of Personal Information” section of Part II of this article.
China has established a personal information and data protection regulatory regime with its legal framework based on the Cybersecurity Law, the Data Security Law, and the Personal Information Protection Law (“PIPL”). These laws provide a regulatory framework for processing and cross-border transfer of personal information and data.
With respect to the detailed regulatory requirements for cross-border transfer of personal information and data, China has also promulgated a series of drafts of regulations, such as the Network Data Security Administration Regulations (Draft for Comment) (“Data Security Administration Regulations (Draft)”). On July 7, 2022, the Cyberspace Administration of China (“CAC”) promulgated the Measures for Security Assessment of Cross-border Transfer of Data (“Assessment Measures”), which will officially take effect on September 1, 2022. The aforementioned regulations, drafts and the issued standards and guidelines jointly constitute China’s legislative approach to supervising cross-border transfer of personal information and data. In addition, China has promulgated and implemented regulations on vehicle industry data security, and published several draft regulations in certain sectors such as finance, industry and information technology (industrial data, telecommunication data and radio data).
II. Comparison of Regulations on Cross-border Transfer of Personal Information and Data: PRC Laws vs. GDPR
1. Overview of the Comparison between the PRC Regulations and GDPR
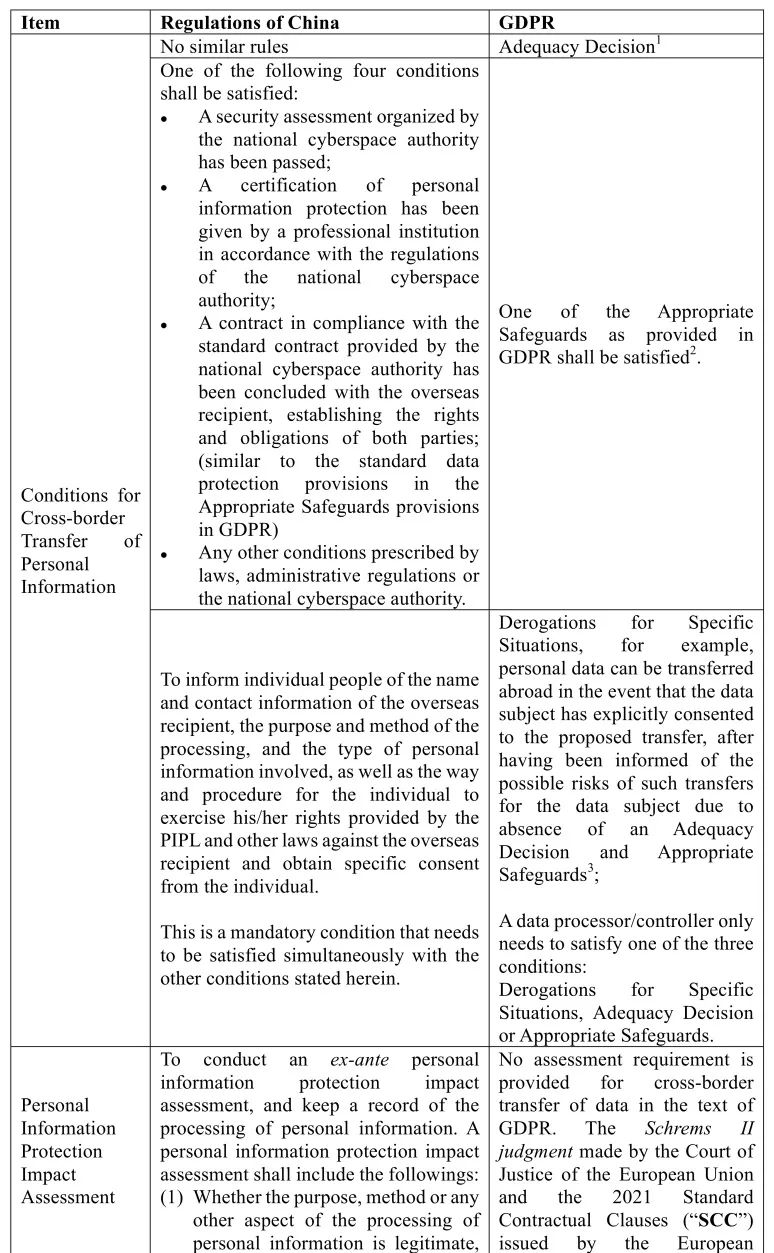
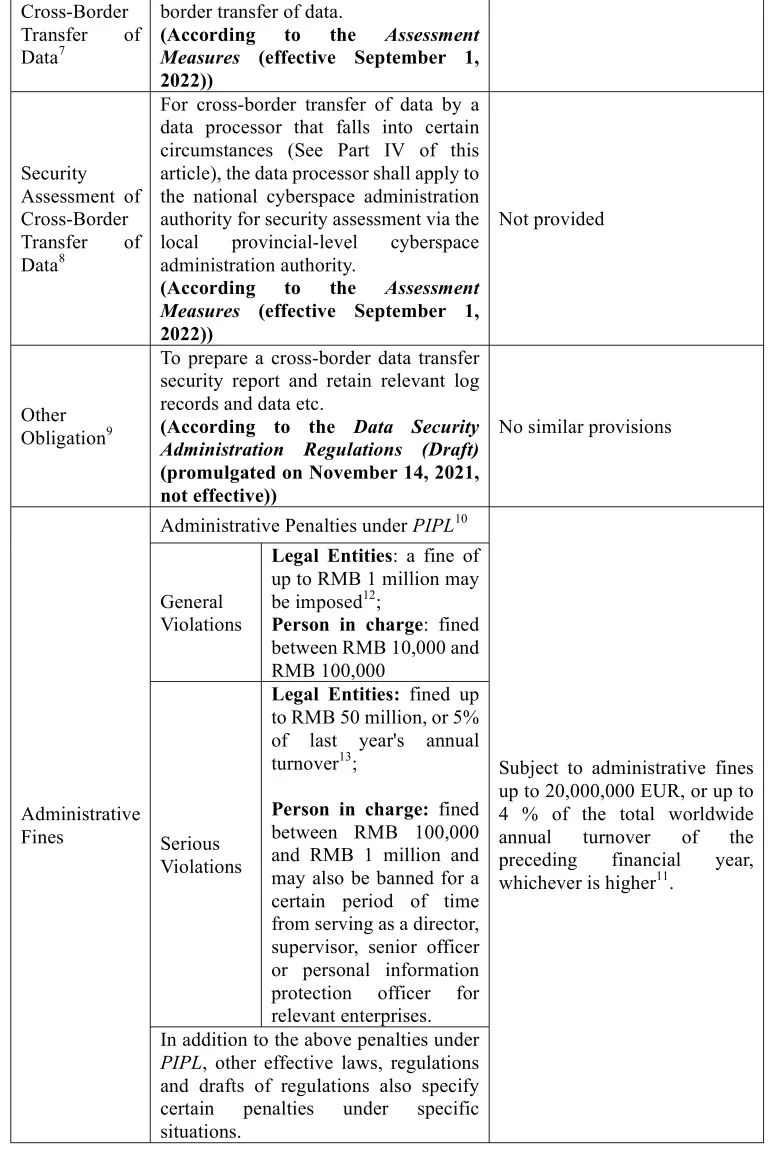
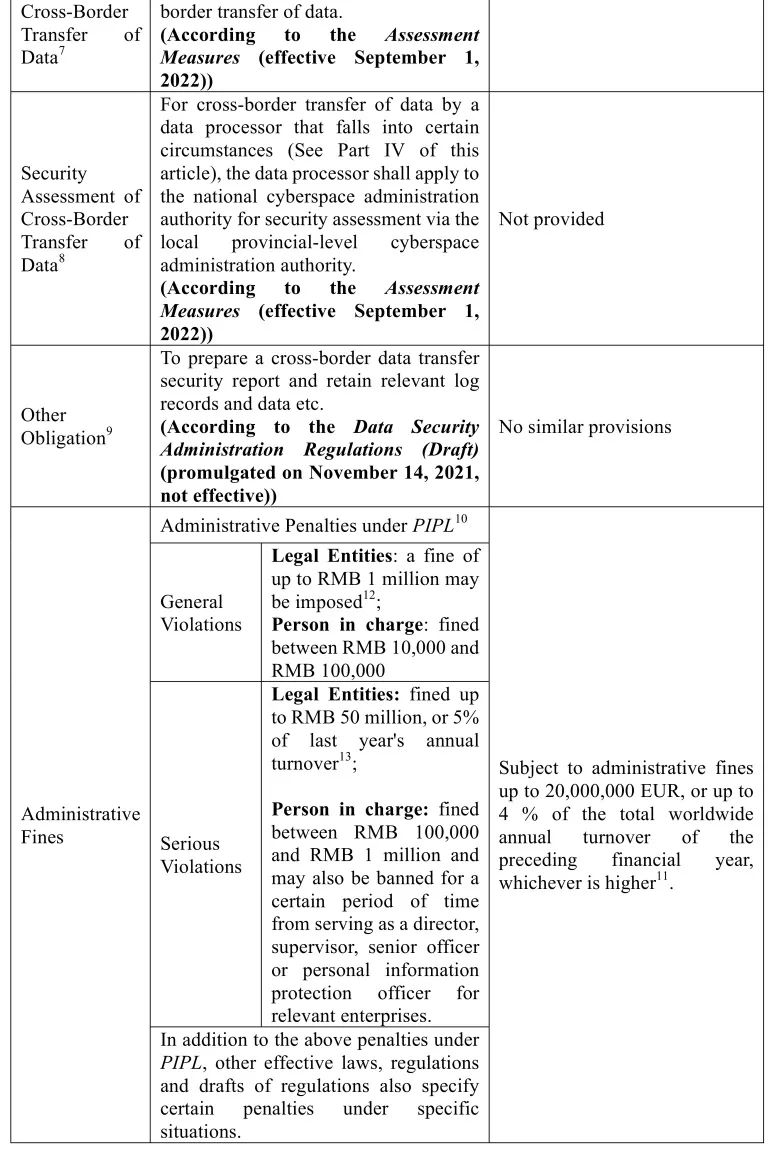
2. Requirements on Cross-Border Transfer of Personal Information
GDPR defines its target of protection as “personal data”, i.e., any information relating to an identified or identifiable natural person (“data subject”). PIPL defines its target of protection as “personal information”, i.e., any kind of information related to an identified or identifiable natural person as electronically or otherwise recorded. GDPR and PIPL both exclude anonymized personal information/personal data from their protection scope. Similar to the definition in GDPR[14], PIPL stipulates that “anonymization” refers to the process in which any personal information is processed to the extent that it cannot be used to identify a specific natural person and cannot be restored to its original state. Any personal information of this nature does not fall under the protection scope of PIPL and thus relevant processors are not required to comply with the provisions of PIPL regarding cross-border transfer of personal information (if any “important data” as described below is involved, relevant provisions shall still be complied with).
As described in the table above, GDPR regulates the circumstances in which data can be transferred abroad in the below three tiers, which are different from China.
(1) Firstly, GDPR adopts the principle of Adequacy Decision[15], i.e., if the European Commission determines that a third country has met the adequate protection standards, personal data can be transferred to such third country without any special authorization process (the whitelist of third countries). China has not yet adopted provisions regarding similar exemption for specific countries.
(2) GDPR further provides that if the condition described in item (1) is not met (i.e., the transfer is not to a white-listed country), data may also be lawfully transferred abroad[16] if the data controller or processor provides Appropriate Safeguards to ensure that adequate data protections have been implemented. China does not have regulations completely comparable to such approach, but to some extent the provision of entering into a standard contract with an offshore recipient under PIPL is similar to the standard data protection clauses as provided in the Appropriate Safeguards provisions under GDPR.
(3) If the aforesaid two conditions are not satisfied, GDPR still provides Derogations for Specific Situations (e.g., where explicit consent of the data subject is obtained, the transfer is necessary for the performance of a contract, for purposes of safeguarding public interests, for the exercise of legal claims, etc.) [17]. China laws do not have such provisions and still require that a specific consent by data subject is a compulsory pre-condition for cross-border transfer of personal information. [18]
In comparison, PIPL provides a more straightforward supervision system for cross-border transfer of personal information, i.e., where it is necessary for personal information to be provided by a personal information processor to an overseas recipient due to any business need or any other need, one of the following conditions shall be met[19]:
(a) A security assessment organized by the national cyberspace authority has been passed before conducting such cross-border transfer;
(b) A certification of personal information protection has been rendered by a professional institution in accordance with the regulations published by the national cyberspace authority;
(c) A contract in compliance with the standard contract provided by the national cyberspace authority has been concluded with the overseas recipient, establishing the rights and obligations of both parties;
(d) Any other conditions prescribed by law, administrative regulations or the national cyberspace authority are satisfied.
In addition, PIPL also requires that personal information processors shall take necessary measures to ensure that offshore recipients’ processing of personal information shall meet the standards of personal information protection provided in PIPL.
3. Requirements on Cross-Border Transfer of Important Data—Security Assessment
In addition to protecting personal information, the PRC legal system also protects data[20]. In practice, there might be some overlaps between the specific content of personal information and data. In some regulations, personal information and data are regulated in the same provisions. PRC laws particularly emphasize the supervision of “important data” in the scenarios of cross-border transfers of data. The Data Security Law provides that China shall establish a categorized and graded data protection system, and carry out categorized and graded data protection in accordance with the degree of importance of data to economic and social development, and the possible damages to national security, public interests, or the legitimate rights and interests of individuals or organizations in the event that data are tampered with, destroyed, leaked, or illegally obtained or used. This categorized and graded data protection regime applies to the protection of important data. The topic of cross-border transfer of important data is one of the focuses under the protection of important data, for which both the Cybersecurity Law and the Data Security Law require complying with the relevant regulations of the national cyberspace authority.
Then, what is the definition of important data? The Assessment Measures clearly state that “important data” means any data, if tampered, damaged, leaked, or illegally acquired or illegally used, may endanger national security, the operation of the economy, social stability, public health and security, etc.[21] In addition, the Data Security Law also stipulates, each region and department shall, in accordance with the categorized and graded data protection system, determine its specific catalogue of important data for the respective region and department, and in relevant industries and areas, and undertake special protection for the data included in the catalogue. At present, except for regulations such as Several Provisions on Vehicle Data Security Administration (for Trial Implementation) that have clear definitions of important data in specific industries, there are not many currently effective regulations providing more comprehensive provisions on the specific description of important data. In the meanwhile, some draft rules for comments such as National Standard “Information Security Technology - Guideline for Identification of Important Data” (Draft for Comment) have explored to define the scope of important data.
While the requirement for security assessment of cross-border transfer of data [22] is included under the Cybersecurity Law (implemented and effective), relevant implementation details are further stipulated under the Assessment Measures (see Part IV of this article for details).
III. Scope of Activities of Cross-border Transfer of Data
On July 7, 2022, the same day of the official promulgation of the Assessment Measures, the CAC press spokesman answered questions regarding the Assessment Measures. The spokesmen explicitly stated that cross-border data transfers mainly include (1) data processors transfer and store data collected and generated in the course of their operations in PRC to overseas; (2) the data collected and generated by the data processor is stored in PRC and institutions, organizations or individuals outside PRC can access or use such data. In addition, we noted that the Information Security Technology - Guideline for Security Assessment of Cross-border Transfer of Data (Draft for Comment) (“Guideline for Security Assessment (draft)”, issued on August 30, 2017) provides that cross-border transfer of data is a one-time or continuous activity in which a network operator provides personal information and important data collected and generated in its operation in China through networks and other means to institutions, organizations or individuals outside China by directly providing or conducting business, providing services, products, etc. [23] Although this guideline was issued prior to PIPL, the Data Security Law and the Assessment Measures, it can still provide certain reference to network operators.
Guideline for Security Assessment (draft) also lists the following different scenarios:
Scenarios that are cross-border transfers of data:
-
Although data is not transferred and stored overseas, it is accessed and visited by institutions, organizations or individuals outside the PRC (except for public information and web access)
For example, remote access to a server of a domestic entity by an offshore entity or an offshore vendor of a multinational company. -
The personal information collected and generated by a network operator (mainly refers to internal data of a company group) in China operation is transferred/stored abroad;
For example, a China entity of a multinational company transfers/stores its employee information, business information, etc. collected by itself to an offshore affiliate. - To provide data to individuals or entities who are located in China but not subject to the China jurisdiction or to entities that are not registered in the PRC.
Scenarios that are not cross-border transfers of data:
- Important data that is neither collected nor generated during operations in PRC is transferred out of PRC in transit only without any changes or processing in PRC.
-
Important data that is neither collected nor generated during operations in PRC is transferred abroad after being stored and processed in the PRC, where no PRC domestic data is involved.
Thus, only if such important data is neither collected nor generated during the domestic operations in PRC and does not involve any domestic data of PRC, will the transfer of such important data not be considered as cross-border transfer of data.
In addition, according to the requirements of the Data Security Administration Regulations (Draft), if it is necessary to further transfer personal information already transferred overseas, the data processor shall reach agreement on the conditions for the further transfer with the individual concerned and establish the security protection obligations to be performed by the data recipient. [24] In addition, on June 30, 2022, the CAC issued the Provisions on the Standard Contract for Outbound Cross-border Transfer of Personal Information (Draft for comments) (the “Provisions on the Standard Contract (Draft)”), which also provide requirements on the further transfer of personal information from an overseas data recipient to another overseas third party, including that such transfer shall be conducted based on genuine business need, that the individual concerned has been informed of the relevant detailed information of such further transfer and such individual’s/individual’s guardian’s specific consent has been obtained, and the overseas data recipient has entered into a written agreement with such overseas third party and provided a copy of such agreement to the PRC personal information processor.
In comparison, GDPR directly stipulates that a cross-border transfer of data not only includes any transfer of personal data to a third country or to an international organization, but also includes any transfer of personal data from a third country or an international organisation to another third country or to another international organisation. [25]
IV. Detailed Analysis of Requirements on Cross-Border Transfer of Personal Information and Data
1. Security Assessment
GDPR does not specifically require security assessment for cross-border data transfers, whereas PRC laws impose such requirement. With the aforementioned Cybersecurity Law and PIPL in place as coded laws, the Assessment Measures that will soon come into effect set forth detailed scenarios where security assessments regarding personal information and data are required, reflecting the current attitude from the regulators on this issue. Specifically, the Assessment Measures state that if a cross-border transfer of data to be conducted by a data processor falls under any of the following circumstances, then the data processor shall apply for a security assessment via the provincial cyberspace administration authority (where the data processor is domiciled) to the national cyberspace administration authority[26]:
(1) cross-border transfer of important data[27] by a data processor;
(2) cross-border transfer of personal information by a critical information infrastructure operator (“CIIO”) or a personal information processor who has processed personal information of more than one million individuals;
(3) cross-border transfer of personal information by a personal information processor who has made cross-border transfers of the personal information of 100,000 people cumulatively or the sensitive personal information of 10,000 people cumulatively since January 1st of the previous year; or
(4) other circumstances where an application for security assessment of cross-border transfers data is required as prescribed by the national cyberspace administration authority.
Based on the above rules, data processors do not need to conduct security assessment for every cross-border transfer of data or personal information. For example, if a non-CIIO domestic entity of a multinational company transfers/backups personal information of its employees and its business information (both non-important data) collected by it to an offshore entity, and the aforementioned threshold is not exceeded, then a security assessment is not required. Only in the event that a transfer involves important data, CIIOs, or data processors who have processed personal information to a certain amount and transfer personal information offshore, will the relevant data processors be required to conduct security assessments.
2. Certification
Although both PRC laws and GDPR include certification as one of the compliant means for cross-border transfer of personal information, the specific certification rules under PRC laws and GDPR are different.
With respect to the certification of personal information protection conducted by professional institutions, China issued the Practice Guide to Cybersecurity Standards - Specification on Certification Technologies for Cross-border Personal Information Processing Activities) (the “Certification Guide”) in June 2022, which provides guidance with respect to the transfer subject to certification, certification bodies, certification means, basic principles and requirements for certification, and protection of the rights and interests of personal information subjects etc.
Specifically, professional institutions’ personal information protection certification for cross-border personal information processing activities applies to the following situations[28]:
(a) Cross-border personal information processing activities among subsidiaries or affiliates of multinational enterprises or those under the same economic or business entities;
(b) Personal information processors’ processing activities outside of PRC of personal information of natural persons in PRC as stipulated in Article 3, Paragraph 2 of PIPL.
We noticed that under scenario (a) above, entities within a group company usually implement similar management systems. Therefore, as an internal group transfer, the certification mechanism can be effectively implemented and can help form a relatively standardized operational protocol within the group for cross-border processing of personal information.
The Certification Guide has not provided some implementing details on requirements for professional certification institutions and certification process, which are to be further clarified by implementing rules.
In comparison, GDPR requires ex-ante certification to be conducted in conjunction with a commitment from the third country data controller or processor to adopt binding and enforceable Appropriate Safeguards, i.e., such third country data controller or processor shall make binding and enforceable commitments, via contractual or other legally binding instruments, to adopting Appropriate Safeguards including those protection measures with regard to the rights of data subjects. This certification mechanism is one of the Appropriate Safeguards required for cross-border transfers of personal data; GDPR sets out details of the relevant requirements for certification, validity period, and certification institutions in Articles 42 and 43. In addition, under GDPR, certification can be used both as an internal compliance arrangement for an enterprise’s daily operations and as the proof that Appropriate Safeguards have been provided. Compared to the China Certification Guide, the GDPR provides more detailed guidance for certification.
3. Standard Contract
European Union has promulgated and has been updating the standard contractual clauses from time to time. As for China, the Assessment Measures list the main points to be included in the contract between personal information processor and overseas recipient[29]. On June 30, 2022, the CAC issued the Provisions on the Standard Contract (Draft), which provide details regarding the applicability of standard contracts, filing requirements, and initial round standard contract clauses, as set forth below.
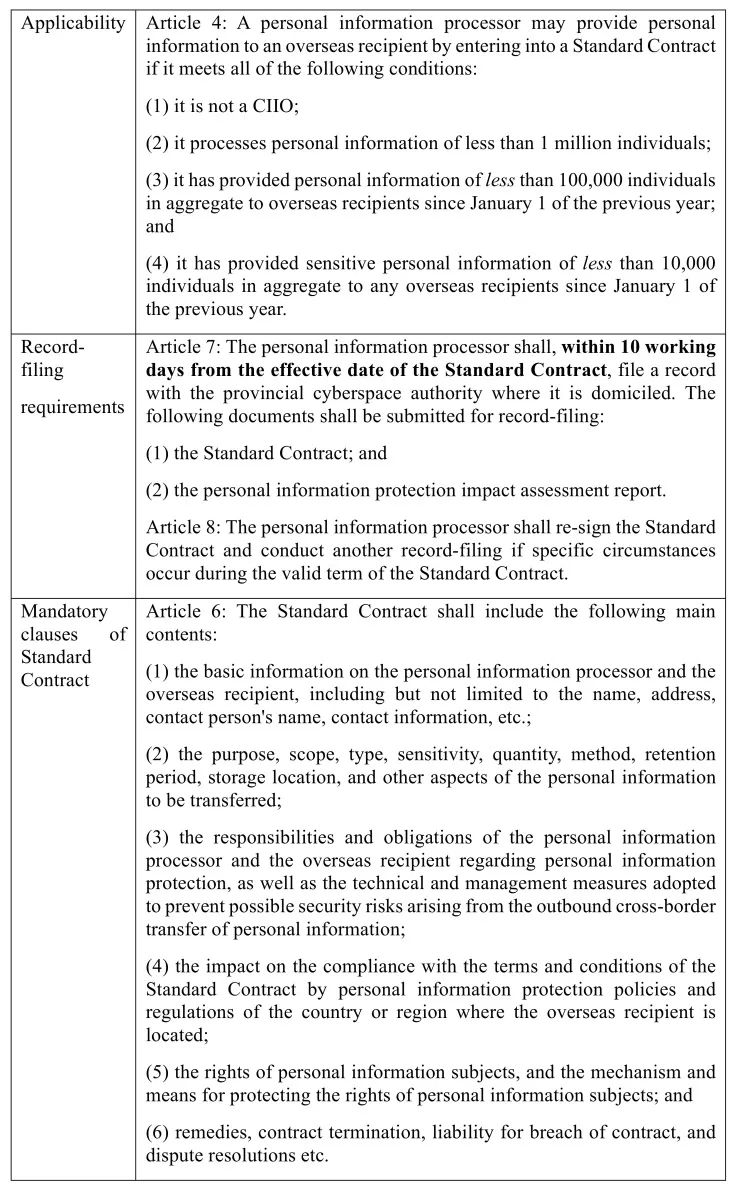
4. Procedure of Security Assessment for Cross-Border Transfer of Data
As mentioned above, for the security assessment of cross-border transfer of personal information and data, the Assessment Measures outline the following process:

V. Data subject’s right to know and consent
Under GDPR, personal data may be transferred abroad if the data subject has explicitly consented to such transfer after having been informed of the possible risks of such transfers on the data subject due to the absence of an Adequacy Decision and Appropriate Safeguards. Thus, such “notification + consent” mechanism is one of the approaches to meeting the requirements of cross-border transfer of data, but not a mandatory requirement.
For cross-border transfers of personal information under PRC laws, the “notification + consent” mechanism is a “must” item rather than an optional exemption by itself, i.e., it is mandatory in addition to the requirements as discussed in Part IV of this article (security assessment, certification, standard contract, etc.). A personal information processor/data processor who is to provide personal information of any individual to a recipient outside of PRC shall inform the individual of the name and contact information of the overseas recipient, the purpose and method of the processing, and the type of personal information involved, as well as the way and procedure for the individual to exercise his/her rights provided by the relevant laws against the overseas recipient, and obtain specific consent from the individual[30]. The Data Security Administration Regulations (Draft), a draft of regulations that has not yet taken effect, also set forth certain details of such “notification + consent” requirement, stipulating that if specific consent has been obtained from an individual for the future cross-border transfer of the person’s personal information at the time of collecting the personal information, then further specific consent from the individual is not required for the cross-border transfer of any personal information covered under that specific consent already obtained.[31] In such cases, given that the individual concerned has given express consent, such consent shall be valid at the time of the cross-border transfer unless such individual withdraws his or her consent prior to the cross-border transfer of the personal information. In practice, if an enterprise is able to determine the specific information for future cross-border transfer of personal information at the time of collection of personal information (and no subsequent changes occur), the enterprise may consider obtaining specific consent from the individual for such cross-border transfer at the time of collecting such personal information to reduce time and labor costs.
VI. Conclusion
China is gradually improving its personal information and data protection regulatory regime. The cross-border transfer of personal information and data is one of the main issues to which multinational companies need to pay attention under China’s gradually escalated supervision and administration on personal information and data protection. Although some of the regulations on cross-border transfers of personal information and data are currently still in draft forms for public comments, multinational companies are suggested to study PRC’s currently effective laws and regulations and draft regulations and plan ahead to update and improve their compliance programs for cross-border transfers of personal information and data according to their business needs, while staying alert to the updates of PRC laws in this area.
Notes:
[1] Article 45 of GDPR
[2] Article 46 of GDPR
[3] Article 49 of GDPR
[4] The Schrems II judgment made by the European Court of Justice states that in addition to applying the standard data protection clauses in the “appropriate safeguards” of article 46, GDPR, a transfer impact assessment analyzing the impacts of a transfer shall be conducted, so as to demonstrate that appropriate protections for the transferred personal data are provided by the laws and practice of the third country where such data recipient locates and the requirements of appropriate safeguards have been met. The European Data Protection Board announced a document regarding recommendations of protection of personal data in 2021, which also follow such requirement. Furthermore, the 2021 version of SCC stipulates that, a transfer impact assessment shall be made and documents of such assessment shall be made available to the competent supervisory authority on request.
[5] Article 48 of GDPR
[6] Article 2 of the Assessment Measures, which was issued on July 7, 2022 and will take effect on September 1, 2022, confirms their scope of application as “the provision by data processors to foreign countries of important data and personal information collected and generated in the course of their operations in the PRC”. On the same day, the Cybersecurity Administration of China further stated the content listed in this column in its press release regarding the Assessment Measures.
[7] This provision in the Assessment Measures is similar to the provision regarding impact assessment of personal information protection under Article 56 of the PIPL, the relationship between these two mechanisms needs to be further clarified by the supervisory authorities.
[8] Article 4 of the Assessment Measures
[9] Article 39 of Data Security Administration Regulations (Draft)
[10] Article 66 of PIPL. In addition, the Cybersecurity Law and the Data Security Law also stipulate relevant penalties for violating the regulations on cross-border transfer of data.
[11] Article 83, section 5 of GDPR
[12] The violator may also be ordered to make a correction, given a warning, and confiscated of any illegal gain by the authorities performing personal information protection duties, and any application program that illegally processes personal information will be ordered to suspend or terminate its services, etc.
[13] The violator may also be ordered to make a correction, be confiscated of any illegal gain; be ordered to suspend any related activity or to suspend business for rectification, and/or be reported to the relevant authority for the revocation of the related business permit or the business license, etc.
[14] Section 26 of Preambles of GDPR, “The principles of data protection should therefore not apply to anonymous information, namely information which does not relate to an identified or identifiable natural person or to personal data rendered anonymous in such a manner that the data subject is not or no longer identifiable.”
[15] Article 45 of GDPR
[16] Article 46 of GDPR
[17] Article 49 of GDPR
[18] Article 39 of PIPL; Article 36 of Data Security Administration Regulations (Draft)
[19] Article 38 of PIPL
[20] Article 3 of the Data Security Law: for the purpose of this law, data shall refer to any record of information in electronic or other form.
[21] Article 19 of GDPR
[22] Article 37 of the Cybersecurity Law
[23] Article 3.7 of Guideline for Security Assessment (draft) (issued on August 30, 2017)
[24] Article 39, Section 9 of Data Security Administration Regulations (Draft)
[25] Article 44 of GDPR
[26] Article 4 of the Assessment Measures
[27] Please refer to the relevant provisions of important data in Data Security Administration Regulations (Draft) and the classified and graded data guidelines in Cybersecurity Standards Practice Guidance - Cyber Data Classification and Grading Guidelines.
[28] Section 1, Application of certification, Certification Guide
[29] Article 9 of the Assessment Measures
[30] Article 39 of PIPL
[31] Article 36 of Data Security Administration Regulations (Draft)
-
 业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Outbound Investment、Compliance & Risk Control、Life Science & Healthcare
业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Outbound Investment、Compliance & Risk Control、Life Science & Healthcare -
 业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Life Science & Healthcare、Compliance & Risk Control、Environment, Social & Governance (ESG)、Digital Economy and Data Security
业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Life Science & Healthcare、Compliance & Risk Control、Environment, Social & Governance (ESG)、Digital Economy and Data Security








