The China Data Security Law, effective from September 1, 2021, defines “data” to be “any recorded information in electronic or other forms[1].” In recent years, from a mere information recording and transmitting carrier, data has gradually become an important resource[2]. The mobility of data is the key to realize the value of data, which necessitates the support from Chinese legislation. Article 19 of the China Data Security Law states that the State shall establish and improve the data transaction administration regime and ensure the legality of data transactional activities at national legislation level. Concurrently, Shanghai municipality and Shenzhen city also officially issued Shanghai Municipal Data Ordinance and Shenzhen Special Economic Zone Data Ordinance, respectively, both on January 1, 2022, at local legislation level, for the purpose of refining the details such as rights and interests regarding data, data transactions, etc.
This article aims to provide a brief analysis of data transactions between enterprises and their major considerations. Due to the diversified commercial utilization models of data in the Big Data era, this article only discusses a limited number of categories of data transfers for value. Case-by-case discussions will be necessary in real practice to determine the appropriate transaction details.
I. Title and Ownership with Transferability of Data
In recent years, China has consecutively promulgated new laws and regulations regulating data protection, represented by the China Data Security Law and the China Personal Information Protection Law (“PIPL”). However, there is no crystal-clear conclusion on how to determine the title and ownership of “data” in both legislation and academic fields to date[3]. It is generally recognized that data is the carrier of information, and information can further generate and contain different knowledge and know-hows. Thus, people may have different views on the nature of particular types of data, and the information contained in data may reflect different types of property rights simultaneously or separately.
The Civil Code: Data transfer not set out as a named contract for civil law protection
Property rights may vest in certain types of data subject to specific conditions[4]. However, as of today, PRC laws still don’t contain a clear definition of ownership or title of data. The Civil Code only states in principle that data rights shall be protected, without detailing how to protect such rights. The China Data Security Law also remains silent on the details of property rights of data[5]. As a result, there are inevitable uncertainties on the contract clauses’ effectiveness and enforceability if those named contracts as listed in the Civil Code (e.g., purchase and sale contract, lease contract, etc.) are “borrowed” as templates to design the clauses of data transaction agreements.
Intellectual Property Statutes: Case-by-case analysis is required to determine whether the data property rights are classified as copyright or trade secrets
Another point of view advocates that “data” should be regulated under the intellectual property law regime. However, since whether specific data (and the information contained within) is an object under the intellectual property law regime is still subject to a case-by-case discussion, it remains uncertain whether the intellectual property law regime can be directly applied to data transfers, and if so, how to apply such regime.
Specifically, there are some differences between data and traditional intellectual properties (e.g., copyright or trade secrets):
First, compared with copyright, data often does not meet the requirements of “work”[6] under the China Copyright Law (Revised in 2020) (the “Copyright law”). In many transactions, most contents of data (especially personal information related data) are records of facts and reflections of objective realities, which cannot easily meet the “originality” requirement[7]. However, relevant public data, nature observations and even statistics data can still be protected under copyright through “categorization and compilation” (e.g., various statistics data compilations, yearbooks, etc.). Therefore, people may not make a general assertion that data could not be commercially utilized and protected as copyrights.
Second, although trade secrets have been protected similar to intellectual properties[8] in China’s legislation and judicial practices, not all types of data can be automatically classified as trade secrets. According to Article 9 of the China Anti-Unfair Competition Law (Revised in 2019) (the “Anti-Unfair Competition Law”), trade secrets refer to commercial information with value for business (such as technical information and business information) that is unknown to the public and has been given confidentiality protection by the rights holder. In the Big Data era, not all types of data can be regarded as trade secrets; some types of data are actually public information as classified, complied or summarized but not kept confidential. Therefore, a case-by-case analysis is needed to determine whether specific types and volumes of data can be characterized as trade secrets and transferred under common licensing arrangements.
China Criminal Law: Data with specific nature is not even transferable
Not all types of data can be freely transferred in China, though it has value. For example, the crime of infringement upon citizen’s person information, stipulated in Article 253 of the China Criminal Law, imposes criminal liabilities on data processor’s specific behaviors: “whoever violates relevant provisions of the State and sells or provides personal information of citizens to others, if such violations are serious, shall be liable to a sentence of imprisonment which is no more than 3 years or detention, with a concurrent or separate monetary penalty; if such violations are particularly serious, the punishment can be up to a 3 to 7 years imprisonment with a concurrent monetary penalty.” “Violation of relevant provisions of the State”, “Sell or provide citizens’ personal information to others” and “Serious violations” are three key objective aspects we need to consider in the actus reus of this crime[9].
Detailed interpretation guidelines on the application of this crime can be found in the Interpretation of Supreme People’s Court and Supreme People’s Procuratorate on Several Issues regarding Application of Law in Handling of Criminal Cases Involving Infringement of Citizen’s Personal Information:
- “Violation of relevant provisions of the State” means “the violation of laws, administrative regulations and departmental rules on the protection of personal information of citizens.” We understand that: transactional activities that violate PIPL will fit above criteria. For example, according to PIPL, a personal information processor is obliged to obtain prior consents of the individual, only with specific express exceptions (e.g., when it is necessary for a person to sign/perform as a party concerned in a contract, or when it is necessary to implement human resource management according to lawfully established labor rules or lawfully signed collective contracts, etc. )[10]; failure to obtain the individual’s consent before processing his/her personal information may constitute this element of crime.
- “Provision of citizens’ personal information” means “the activities of providing personal information of citizens to particular persons, and the activities of releasing such information through the information network or other channels” and “provision of ‘lawfully collected’ personal information of citizens to others without the consent of the persons whose information is collected; unless the processed personal information cannot be identified to specific individual, and such anonymity of personal information is unrecoverable” (this exception is consistent with “anonymity” prescribed in Article 73 of PIPL).
- “Serious violations” has various ways of expressions, one of which is its low threshold regarding to the number and amount of personal information transactions (RMB 5,000 only, approximately equivalent to USD 740), and it is not difficult to meet this threshold in practice. It is worth noting that “illegal acquisition” and the sale or provision of a certain amount of specific personal information of citizens can be regarded as one scenario of “serious violations”. Therefore, the data provider in a data transaction of personal information must guarantee the lawful origin of the subject matter data[11].
In summary, we hold the view that a case-by-case analysis is needed to determine whether data can be transferred and whether data can be categorized as a kind of specific objects protected by laws. For this purpose, we have prepared the following summary as a simple comparison:
Table I:
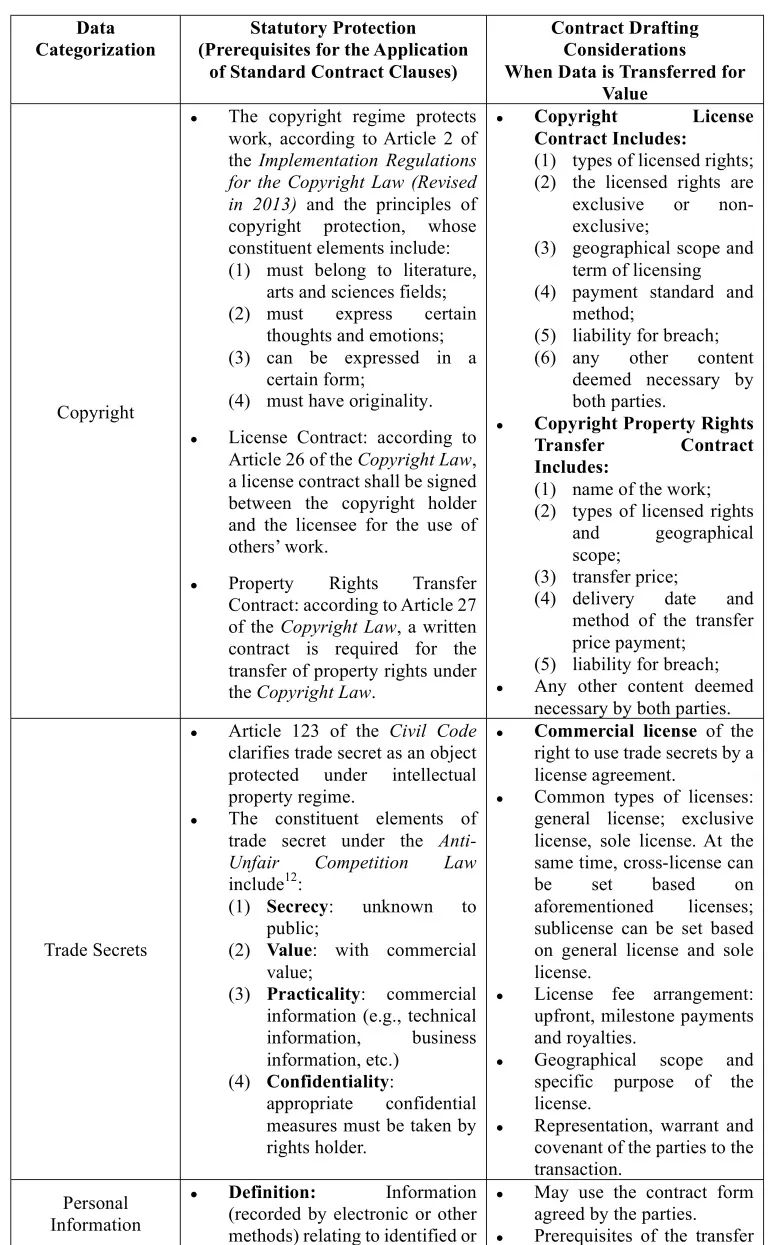

When a data transaction for value does not have above characteristics and falls outside of the regulatory framework listed in the laws and regulations above, the parties will need comprehensive discussions on the terms and conditions of data transaction contract in order to make it suitable for specific scenarios. Next, we will briefly introduce the key points in drafting data transfer agreements.
II. Pricing in Data Transaction
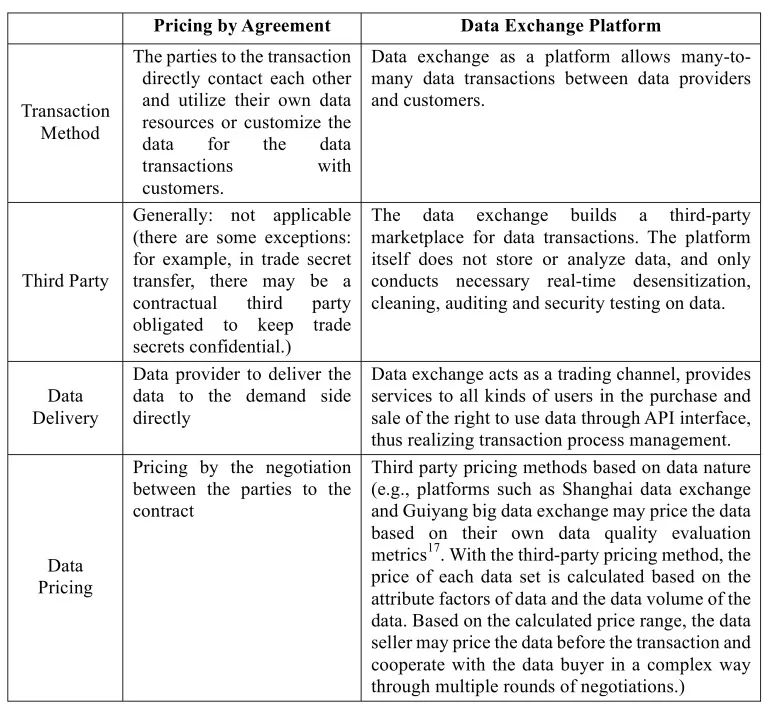
As discussed above, data products are similar to intangible assets in nature. Therefore, for the valuation of data products, in theory the valuation methods applicable to intangible assets could be referred to, such as the cost method, the income method or the bench-to-market method, etc. Of course, considering the special characteristics of the valuation of data products (for example, some kinds of data can only have commercial values in narrow and specific scenarios) and the user’s own subjective judgement on the value of specific data, now it is more common for the parties to value the data by agreement.
In additional to traditional contractual pricing between the parties, data exchange platforms are becoming an important channel for the data transaction and have become one of the major initiatives to facilitate the mobility of data resources across the country. The following diagram is a brief comparison of some basic differences between the pricing by agreement model and the data exchange platform pricing model for readers’ reference. It is worth noting that the parties to the transaction may also consider agreeing on corresponding liquidated damages in the contract, so that the non-breaching party may claim the liability for breach of contract towards the breaching party.
Table 2:
III. Other Key Points in Drafting Data Transaction Agreements
1. Common Forms of Data Transaction Agreements
By License: Better option if the data to transfer for value can be categorized as trade secrets
We may use the form of trade secrets license agreement in drafting data transfer agreements since trade secrets are statutory intellectual properties. Trade secret license agreements enable the licensor to reuse the right to use trade secrets and other property rights and interests by retaining the ownership. For the licensee, the license agreement can facilitate its development and launch of relevant products if the licensee lacks relevant professional technologies, time and efforts. As we have discussed above, trade secret license arrangements are more flexible and the parties concerned may choose the license terms according to their actual transaction needs. In addition, license transactions often contain milestone payment terms that help flexibly arrange the transaction milestones and avoid disputes or unnecessary losses to the greatest extent possible.
By Transferring: Better option if the data to be transferred for value has originality
Under certain circumstances, some types of data may not be illegally sold or provided to others as stated in the Article 253 of the Criminal Law. However, on the other hand, since the existing laws and regulations do not specify the exact property right attached to data (e.g., determining ownership title), in practice, we understand that: when the subject matter of proposed data transaction has originality or has the attributes of “work” under the Copyright Law, the parties to the transaction may also consider a transaction for value to be structured as copyright license or transfer. In such cases, the data provider may only transfer the property rights in the data copyrights to the data transferee or licensee[18].
By Services: Better option if the data to transfer for value is not explicitly classified under specific laws and regulations
In addition, some data transactions can also be carried out in the form of data service, especially for the services in which the data provider provides certain data service to clients for a fee on a Data-as-a-Service (“DaaS”) basis. If a data transaction between the data provider and the data demanding side is carried out in a DaaS arrangement, the data provider’s obligations are mainly to provide data service to clients, mostly in the form of providing on-demand data from various sources via API, aiming to simplify the access to data and provide data sets or data streams that can be used in different formats.
In our view, one of the business significances of DaaS type data service agreement is to provide an approach to use restricted data indirectly. Considering the background that major economics in the world have published laws and regulations restricting cross-border data transfer, it is likely the data transaction between the parties may be subject to cross-border transfer restrictions; and such data to be transferred across borders (especially important data and sensitive personal information under Chinese laws) may be required to stay within a specific jurisdiction and cannot move freely. In this case, the data demanding party may purchase analytics deliverables, rather such data itself, through DaaS services from a third-party data processing organization that desensitizes the data and provides the clients with analysis and statistics reports on the restricted data through data service agreements.
Others: In addition to these common data transaction arrangements, in practice, there are also cases where specific inseparable physical objects and related data are jointly transferred. For example, the parties to the transaction are collaborating in the development of a prototype product (medicine or machine, etc.), and the provider delivers the product, cells, blood products, sample prototype and other tangible subject matters along with (and necessary) relevant data to the counterparty. There is no “market norm” conclusion on the choice of form of contractual arrangements in this type of business collaboration in terms of data transfer, and the parties may wish to discuss on a case-by-case basis in accordance with actual needs.
2. Cross-border data transfer under data transaction agreements
The drafting and design of data transaction agreement terms are subject to not only the business needs of a specific data transaction but also mandatory laws and regulations (e.g., the Security Assessment Measures for Outbound Data Transfer to be effective on September 1, 2022, etc.). Particularly, if transaction activities involve cross-border transfers of following types of data:
Table 3:
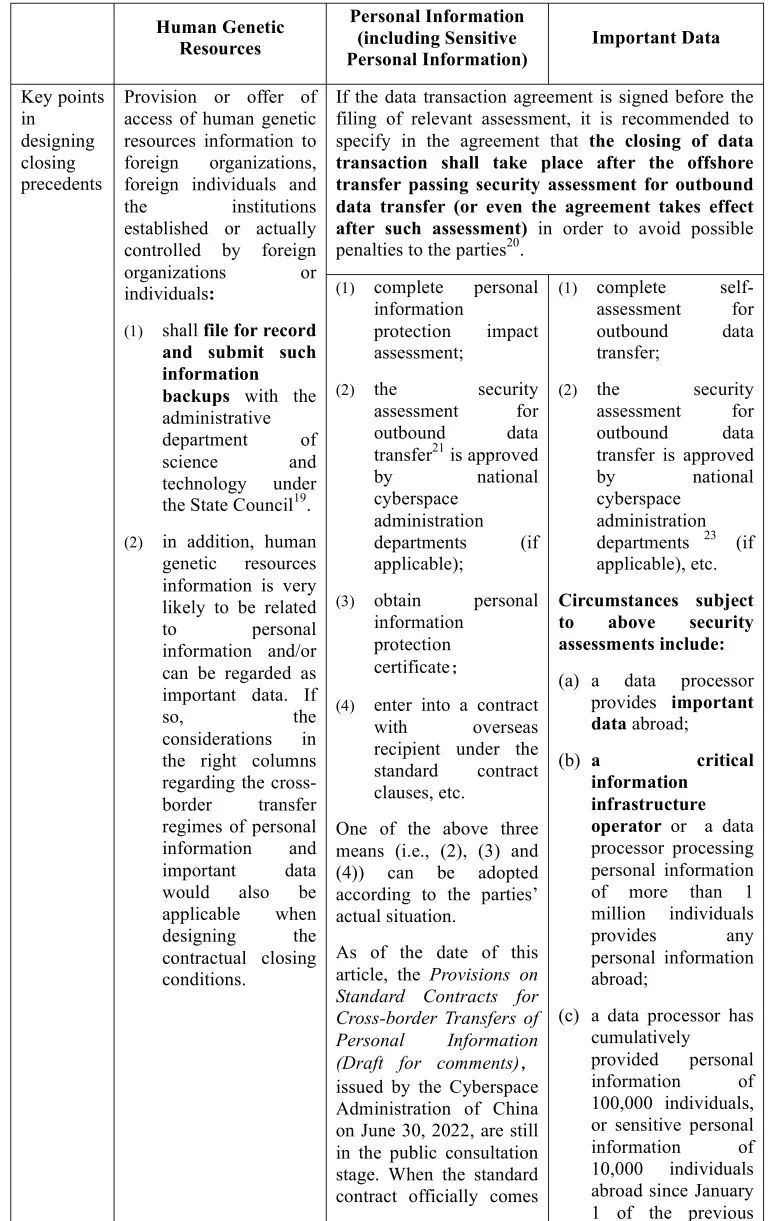
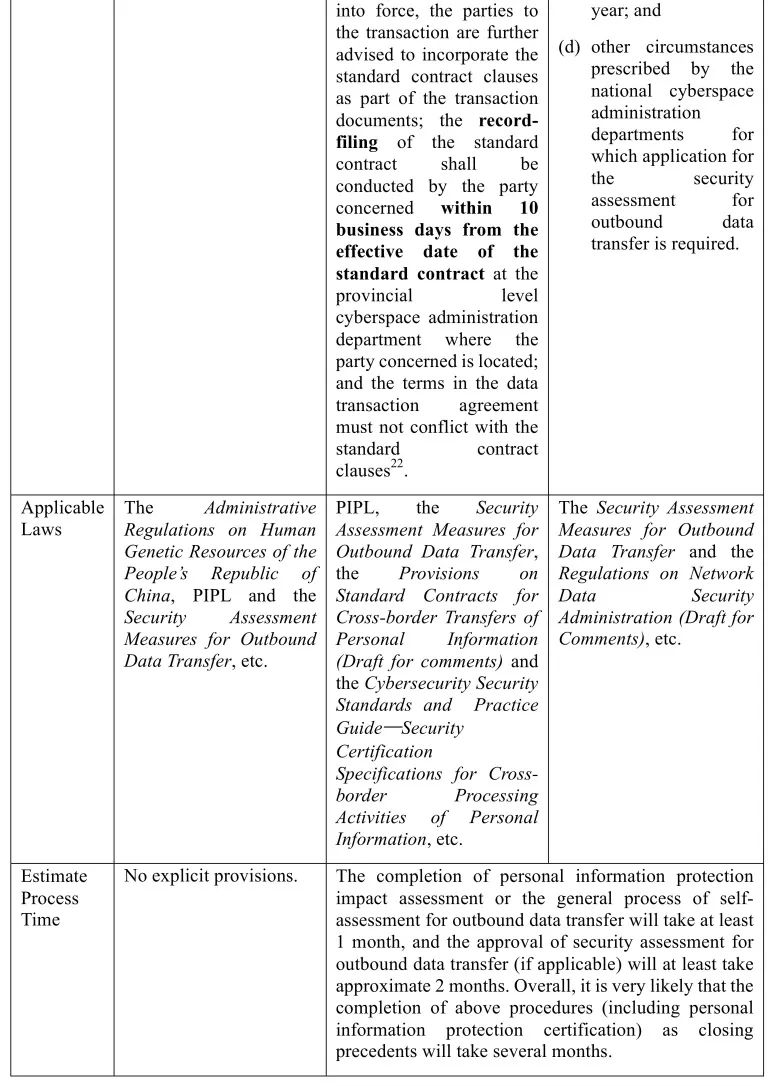
IV. Conclusion
The value of data mainly lies in its commercial utilization and mobility. As China’s laws and regulations in data protection evolve, more and more China-related data transactions will be seen. Data transactions for value and corresponding cross-border transfers will be the main concerns for MNCs to consider in China’s gradually improving and upgrading personal information and data regulatory environment. We will continue tracking the statutes and regulatory updates in China’s data transaction area and share our insights thereon in our future publications.
Notes:
[1] Article 3, the Data Security Law
[2] https://new.qq.com/omn/20210501/20210501A0095P00.html: “As the core resource of the digital economy and information society, data is known as “the oil and diamond mine of the 21st century” and has become one of the five factors of production along with land, labor, capital and technology, and is gradually having a profound impact on national governance capacity, economic operation mechanism and social lifestyle. It is gradually having a profound impact on national governance capacity, economic operation mechanism and social lifestyle.”
[3] http://iolaw.cssn.cn/fxyjdt/201805/t20180517_4659286.shtml, Data Property Rights and Legal Characteristics, LI Aijun, Oriental Law, Vol 3, 2018
[4] Article 127, the Civil Code: where the law contains provisions in respect of the protection of data and network virtual property, such provisions shall apply.
[5] https://www.panewslab.com/zh/articledetails/twxvxumc8b0f.html, Background and Significance of Data Rights, Shanghai Blockchain Technical Association
[6] Article 3, the Copyright Law
[7] Article 2, the Implementation Regulations for the Copyright Law (Revised in 2013)
[8] Article 123, the Civil Code: a civil subject enjoys intellectual property in accordance with the law. Intellectual property is a proprietary right enjoyed by a holder in accordance with law in respect of the following objects: …(five) Trade secrets; …
[9] For your reference: the excerpt of court’s opinion on a criminal trial of LIU Yin and ZHANG Xiang on the crime of infringement upon citizens’ personal information: “The Court held that the defendants’ provision of personal information to others has constitute the crime of infringement upon citizen’s person information…the act of providing citizens’ personal information to others constitutes the crime and is not premised on illegal acquisition …”
[10] Article 10, PIPL
[11] Article 5, the Interpretation of Supreme People’s Court and Supreme People’s Procuratorate on Several Issues regarding Application of Law in Handling of Criminal Cases Involving Infringement of Citizen’s Personal Information: Illegal acquisition, sale or provision of citizens' personal information under any of the following circumstances shall be deemed as "serious circumstances" as stipulated in Article 253 of the Criminal Law: …(seven) illegal gain is more than RMB 5,000.
[12] Article 9, the Anti-Unfair Competition Law
[13] Article 4, PIPL
[14] Article 10, PIPL
[15] Article 23, PIPL
[16] Article 28 and 29, PIPL
[17] http://html.rhhz.net/buptjournal/html/20190118.htm, Data Pricing Mechanism Status and Development Trend, PENG Huibo, ZHOU Yajian, Journal of Beijing University of Posts and Telecommunications.
[18] Article 10, the Copyright Law
[19] Article 28, the Administrative Regulations on Human Genetic Resources of the People’s Republic of China
[20] Answers to the journalists’ questions on the Security Assessment Measures for Outbound Data Transfer
[21] Article 40, PIPL
[22] Article 2, the Provisions on Standard Contracts for Cross-border Transfers of Personal Information (Draft for comments)
[23] Article 4, the Security Assessment Measures for Outbound Data Transfer
-
 业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Life Science & Healthcare、Compliance & Risk Control、Environment, Social & Governance (ESG)、Digital Economy and Data Security
业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Life Science & Healthcare、Compliance & Risk Control、Environment, Social & Governance (ESG)、Digital Economy and Data Security -
 业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Outbound Investment、Compliance & Risk Control、Life Science & Healthcare
业务领域: Corporate / Merger & Acquisition、Private Equity & Investment Funds、Outbound Investment、Compliance & Risk Control、Life Science & Healthcare








