Introduction
With the beginning of an era of the three-pillared data legislation, i.e., the Cybersecurity Law, the Data Security Law and the Personal Information Protection Law of the People’s Republic of China (“PRC”) and further improvements of relevant supporting laws and regulations, departmental rules, and national standards, the data compliance regulating regime in China has shown acceleration in new legislative trends, more focused law enforcement, and more stringent administration of cross-border data transfer for Chinese companies seeking overseas listing.
In July 2021, the Cybersecurity Review Office announced that it had started cybersecurity investigations on three Chinese network platform giants. Immediately following that, the PRC Cybersecurity Review Measures were amended with significant revisions, as a result of which, the importance of cybersecurity review regime started to receive wide attention. Prior to the July 2021 incidents, critical information infrastructure operators (“CIIOs”) were the main market players paying close attention to the Cybersecurity Review Measures; however after such recent incidents, the capital market has also started paying more attention to the cybersecurity review regime. On June 23, 2022, the PRC Cybersecurity Review Office arranged a regulatory meeting with the head of a well-known PRC academic journal database operator and announced that it had started a cybersecurity review on it, which shows the different ways in which cybersecurity reviews can be initiated[1]. With this background, it should now be clear to all that the cybersecurity review regime has become a powerful tool for PRC authorities to comprehensively review the cybersecurity and data security compliance of business operators and impose mandatory rectifications. All kinds of business operators are advised to make themselves fully updated with the constantly evolving regulatory requirements, stay alert to the compliance of red flags, and make timely adjustments and improvements according to their own specific situation.
To present the full landscape of the PRC cybersecurity review regime, we will write a series of articles to provide a comprehensive overview of the evolution of the cybersecurity review regime, the key review points and review procedure, and the key points of compliance for enterprises seeking overseas listing during their listing process. This article is the first in this series, aiming to provide a summary of the evolution of the PRC cybersecurity review regime and its key review points.
I. The Evolution of the Cybersecurity Review Regime
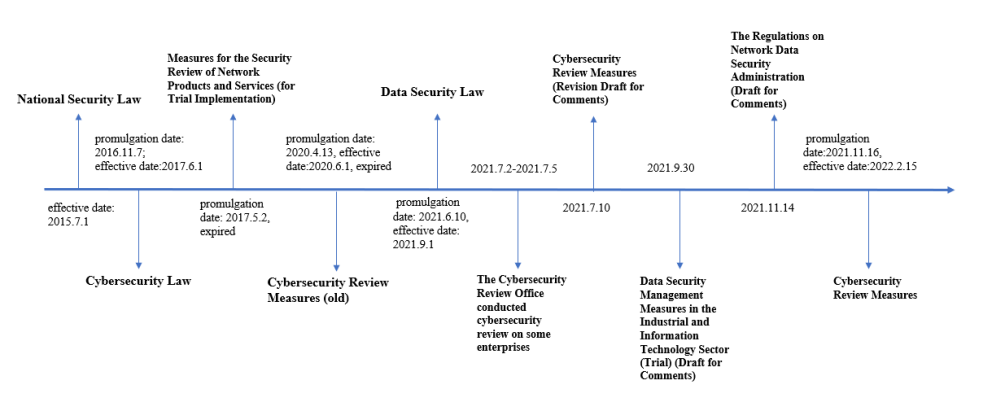
The origin of China’s cybersecurity review regime can be traced back to the National Security Law of the People’s Republic of China (the “National Security Law”) that came into effect in 2015. Article 59 of the National Security Law stipulates that the state shall establish systems and mechanisms for national security examination and supervision, carry out national security examination on foreign investment, specific product items, key technology, network information technology products and services, construction projects related to national security, and other significant activities and events, so as to effectively prevent and eliminate national security risks.
In November 2016, the Standing Committee of the National People’s Congress promulgated the PRC Cybersecurity Law that came into effect on June 1, 2017. Article 35 of the PRC Cybersecurity Law requires that where CIIOs purchase network products and services that might impose risks to national security, they shall go through security reviews administered by the national cyberspace administration authority together with relevant departments under the State Council.
On April 13, 2020, the Cyberspace Administration of China (“CAC”), together with 11 other departments under the direct leadership of the State Council, issued the Cybersecurity Review Measures that require a CIIO’s procurement of any network product or service that affects or may affect national security to be subject to a cybersecurity review under the Measures. Those Measures also repealed the Measures for the Security Review of Network Products and Services (for Trial Implementation) issued on May 2, 2017, which limited the compulsory network security review to important network products and services procured for network and information systems related to national security.
On July 2, 2021, the Cybersecurity Review Office issued an announcement to initiate a cybersecurity investigation on an online car-hailing platform company[2]. Subsequently, CAC, together with six other ministries and commissions, jointly conducted an on-site cybersecurity investigation on this company to examine whether this platform company had complied with the National Security Law, the Cybersecurity Law, and the Cybersecurity Review Measures. During this investigation process, this platform company was ordered to suspend new user registration. During the same period, CAC also initiated cybersecurity investigations on two other network platform companies.
On July 10, 2021, CAC released a revised draft of the Cybersecurity Review Measures for public comments (the “Revised Draft of Review Measures”). The Revised Draft Review Measures expand the scope of the cybersecurity review to include all data processors collecting or generating data within mainland of China that may affect national security, thereby clarifying that the cybersecurity review will cover both cybersecurity and the security of data processing activities. In addition, Article 6 of the Revised Draft of Review Measures stipulates that any operator seeking overseas listing must apply to the Cybersecurity Review Office for a cybersecurity review if it is in possession of personal information of more than 1 million users. Meanwhile, the Revised Draft of Review Measures further clarify that if any data processing activities conducted by data processors affect or may affect national security, the data processors should also conduct cybersecurity reviews. Cybersecurity reviews are divided into two main categories, one category regulating risks of core data, important data or large amounts of personal information being stolen, leaked, destroyed and illegally used or transferred offshore, and the other category regulating risks of critical information about infrastructure, core data, important data or large amounts of personal information being manipulated, controlled or maliciously used by foreign governments after the processors’ offshore listings.
The Data Security Law, which came into effect on September 1, 2021, continued with the legislative trend of expanding the application scope of cybersecurity review in the Revised Draft of Review Measures. Article 24 of the Data Security Law provides that “national security review shall be conducted on data processing activities that affect or may affect national security”, through which, the regulated targets of cybersecurity review are confirmed by effective laws, i.e., including not only CIIOs as stipulated under the Cybersecurity Law, but also all data processors carrying out data processing activities.
The Ministry of Industry and Information Technology (“MIIT”) issued the Data Security Management Measures in the Industrial and Information Technology Sector (Trial) (Draft for Comments) on September 30, 2021, which follows the legislative concept of the Data Security Law on national security review on relevant data processing activities and clarifies that MIIT should carry out data security reviews on industrial and telecommunications data processing activities that affect or may affect national security. Therefore, if the data processing activities affect or may affect national security, then the relevant enterprises might be subject to security reviews by both MIIT and CAC under the national data security work coordination mechanism.
On November 14, 2021, CAC published the revised Regulations on Network Data Security Administration (Draft for Comments), which finetune the provisions in the Cybersecurity Law, the Data Security Law and the Personal Information Protection Law. One of the key provisions are the cybersecurity review obligations set forth in Article 13 of the Regulations on Network Data Security Administration (Draft for Comments), which reads “[i]n the following cases, a general data processor shall apply for a cybersecurity review: (1) a merger, reorganization, or division to be conducted by a network platform operator who has accumulated and controlled a large amount of data resources that pose risks on national security, economic development or the public interests, which will or may affect national security; (2) an overseas listing in a foreign country by a data processor processing the personal information of more than one million individuals; (3) a listing in Hong Kong by a data processor, which will or may affect national security; or (4) other data processing activities that will or may affect national security.
On December 28, 2021, CAC announced the revised Cybersecurity Review Measures (“Review Measures”), which came into effect on February 15, 2022. Compared to the earlier Revised Draft of Review Measures announced on July 10, 2021, the 2022 Review Measures expanded on the earlier Revised Draft of Review Measures by clarifying the triggering events for statutory application for cybersecurity review, including:
(1) When CIIOs procure any network product or service, they shall judge in advance the national security risks that may result in when the product and service are put into use; if the CIIOs, after pre-judging, believe such products or services affect or may affect national security;
(2) When network platform operators conduct data processing activities, if such activities affect or may affect national security;
(3) Internet platform operators seeking overseas listing holding more than 1 million individuals’ personal information.
Article 16 of the Review Measures also add a new review initiation mechanism—the Cybersecurity Review Office’s ex officio review—i.e., if any network products and services or data processing activities are believed by the member organizations of the cybersecurity review mechanism to affect or may affect national security, then the Cybersecurity Review Office will initiate a review, upon reporting to and obtaining approval from the Central Cyberspace Affairs Commission following the established procedure. In order to prevent compliance risks, the involved parties shall take measures to prevent and mitigate risks during the review process in accordance with the requirements of the cybersecurity review. The Review Measures also adjust the required materials to be submitted by the parties in their security review applications and the security risk factors to be assessed, etc.
We prepared the following timeline to show the evolution of the cybersecurity review regime for your reference:
II. Key points in Cybersecurity Review
1. Applicable Subjects
The first category of applicable subjects are CIIOs. According to the Review Measures, when CIIOs purchase network products and services (mainly including core network equipment, important communications products, high-performance computers and servers, mass storage devices, mega databases and application software, network security equipment, cloud computing services, and other network products and services that have a significant impact on critical information infrastructure security, network security and data security), they should pre-judge the risks or possible risks on the national security risk after such purchased products and services are put into use. If such products and services affect or may affect national security after they are put into use, CIIOs should apply to the Cybersecurity Review Office for cybersecurity reviews. Critical information infrastructure refers to public communications and information services, energy, transportation, water conservancy, finance, public services, e-government, national defense science and technology industry, as well as some other important industries and sectors that may seriously endanger national security, national livelihood, public interests of important network facilities and information systems once being damaged, suffering mal-function or data leakage. According to the Regulations on the Security Protection of Critical Information Infrastructure, the competent departments and supervisory and administrative departments of important industries and sectors will be responsible for the organization and identification of critical information infrastructures in such industries and sectors according to the identification rules, and notify the operators the identification results and report such results to the public security department under the State Council in a timely manner.
The second category of applicable subjects are network platform operators. According to the Review Measures, network platform operators shall take the initiative to apply for cybersecurity review in the following two types of scenarios: carrying out data processing activities (including activities such as collection, storage, using, processing, transmission, provision and disclosure of data) that affect or may affect national security; and overseas listing of network platform operators that possess personal information of more than one million users. Although the Review Measures do not clarify the definition of “network platform operator”, the Regulations on Network Data Security Administration (Draft for Comments), published by CAC, define a “network platform operator” as “a data processor that provides network platform services such as information publishing, social networking, transactions, payments, or audio-visual services”. As the Regulations on Network Data Security Administration (Draft for Comments) are still undergoing public consultations and have not been officially issued, business operators can refer to this definition as a preliminary assessment as to whether they might be identified as “network platform operators”. However, whether a business operator will be identified as a network platform operator needs to be clarified by the relevant authorities through future published rules.
Third, according to the Review Measures, if a member organization of the cybersecurity review mechanism believes that a network operator has any network product or service or engages in any data processing activity that affects or may affect national security, the Cybersecurity Review Office may initiate a review on such network operator after it reports it to and obtains approval from the Central Cyberspace Affairs Commission by following the established procedure. Similarly, the Review Measures fail to provide a clear and referable definition of “affect or may affect national security”, thus leaving the determination of such activity to the authorities in charge. The following review key points of the Cybersecurity Review Office are for reference:

2. Initiation Method
According to the Review Measures, a cybersecurity review may be initiated by a proactive application or the Cybersecurity Review Office’s ex officio review.
The first way to initiate a review is through proactive application. As discussed, reviews through proactive application mainly include three categories: (1) a CIIO, when procuring a network product or service, shall pre-judge any risks on national security after such products or services are put into use. If national security will be affected or may be affected, the CIIO shall apply to the Cybersecurity Review Office for a cybersecurity review; (2) a network platform operator conducting data processing activities, which affect or may affect national security, shall apply to the Cybersecurity Review Office for a cybersecurity review; or (3) a network platform operator that holds more than one million individuals’ personal information shall apply to the Cybersecurity Review Office for a cybersecurity review when it seeks to list overseas.
For a review through proactive application, according to Article 8 of the Review Measures, the party concerned shall submit the following materials when applying for a cybersecurity review: (1) a written application; (2) an analysis report on the impact or potential impact on national security; (3) the procurement document, agreement, contract to be executed, or initial public offering (IPO) and other listing application documents to be submitted; and (4) any other material required for the cybersecurity review.
The second way to initiate a review is by ex officio review. According to Article 16 of the Review Measures, any network product or service or any data processing activity that affects or may affect national security as believed by member organizations of the cybersecurity review mechanism shall be subject to a review under the Review Measures after the Cybersecurity Review Office reports it to and obtains approval from the Central Cyberspace Affairs Commission by following the established procedure. Upon receiving of any whistleblowing report, the Cybersecurity Review Office can increase its supervisory role prior to, during, and after the relevant event. For example, if the Cybersecurity Review Office believes that a reported product or service or a data processing activity has resulted or may result in risks to national security, it may initiate the review process in accordance with the Review Measures.
3. Authorities in charge of the Review
According to the Review Measures, the Cybersecurity Review Office set up under CAC is responsible for formulating the relevant policies and rules on cybersecurity reviews and organizing cybersecurity reviews. CAC is vested with authority to establish a national cybersecurity review mechanism, jointly with the National Development and Reform Commission of the People’s Republic of China, the Ministry of Industry and Information Technology of the People’s Republic of China, the Ministry of Public Security of the People’s Republic of China, the Ministry of State Security of the People’s Republic of China, the Ministry of Finance of the People’s Republic of China, the Ministry of Commerce of the People’s Republic of China, the People’s Bank of China, the State Administration for Market Regulation, the National Radio and Television Administration, the China Securities Regulatory Commission, the National Administration of State Secrets Protection, and the State Cipher Code Administration.
Compared with the previous Revised Draft of Review Measures, the Review Measures deleted the reference to “critical information infrastructure protection work department”. Therefore, according to the Review Measures, the Cybersecurity Review Office will become the authority conducting network security reviews, by working jointly with the cybersecurity review mechanism member organizations. In practice, the actual routine administrative work is entrusted by the Cybersecurity Review Office to the China Cybersecurity Review Technology and Certification Center (“CCRC”). CCRC, under the supervision and guidance of the Cybersecurity Review Office, undertakes such tasks as receiving application materials and conducting formality reviews of the application materials. Therefore, the department in charge of receiving applications and consultation related to the aforementioned materials is the CCRC.
4. Process and Key Points of Cybersecurity Review
According to the Review Measures, the process of a cybersecurity review initiated by a party’s proactive application includes application documents submission, application documents review, preliminary case review, comments feedback and special case review procedures. For detailed rules and timeline, please see Diagram 1. The Cybersecurity Review Office may conduct the cybersecurity review ex officio if any network product or service or any data processing activity that affects or may affect national security as believed by member organizations of the cybersecurity review mechanism, the process of which is summarized in Diagram 2.
According to Article 10 of the Review Measures, the Cybersecurity Review Office’s key review points include:
-
Risk that might result from any critical information infrastructure being illegally controlled, tampered with, or sabotaged after a network product or service is used;
-
Risk that a supply interruption in the supply of a network product or service may have in endangering the continuity of any critical information infrastructure;
-
The security, openness, transparency, diversity of supply sources, reliability of any supply channel of the network products or services, and the risk of its supply being interrupted due to political, diplomatic, trade or other factors;
-
Compliance by the provider of the network products or services with the laws, administrative regulations, and departmental rules of China;
-
Risk that might result from any core data, important data or a large amount of personal information being stolen, leaked, destroyed, illegally used, or illegally transferred abroad;
-
Risk that might result from any critical information infrastructure, core data, important data, or a large amount of personal information being affected, controlled, or maliciously used by foreign governments, as well as any network information security risk; and
-
Any other factor that may endanger the security of any critical information infrastructure, network security or data security.
Diagram 1 Review Process of Proactive Application Initiated by the Party Concerned

Diagram 2 Process of Ex Officio Cybersecurity Review by Authorities in Charge

5. Consequences of Violations
According to the Review Measures, an operator who shall apply for a review but chooses not to do so or chooses not to cooperate with the authorities in charge shall be penalized under the Cybersecurity Law of the People’s Republic of China and the Data Security Law of the People’s Republic of China. Specifically, according to Article 65 of the Cybersecurity Law, where CIIOs use network products or services that have neither been examined for security nor passed the security examination, they shall be ordered by the relevant competent departments to stop using such products or services, and be imposed a fine of no less than one but no more than ten times of the purchase price; as for the persons directly in charge or other directly responsible persons, a fine of no less than RMB 10,000 but no more than RMB 100,000 shall be imposed.
According to paragraph 2 of Article 45 of the Data Security Law, those who violate the state administration of core data and thus cause harm to the national sovereignty, national security and development interests shall be imposed a fine of no less than RMB 2 million but no more than RMB 10 million by relevant departments in charge, and shall be ordered to suspend relevant businesses or stop operation for rectification, or be subject to revocation of relevant business permits or business licenses based on the violation; if a crime is constituted, they shall be pursued on criminal liabilities in accordance with the laws. According to paragraph 1 of Article 48 of the Data Security Law, those who refuse to cooperate in data retrieval or submission shall be ordered to make correction and given warnings and may be imposed a fine of no less than RMB 50,000 but no more than RMB 500,000 by relevant competent departments; the management team members directly responsible and other directly responsible persons shall be imposed a fine of no less than RMB 10,000 but no more than RMB 100,000.If an enterprise chooses to proceed with an overseas listing though it falls under the scope of prohibited circumstances for an overseas offering and listing enumerated under Article 7 of the Administration of Overseas Securities Offering and Listing by Domestic Companies (Draft for Comments) (including the offering and listing that are determined after review to constitute a threat to or endanger national security), the securities regulatory authority under the State Council and competent authorities in charge under the State Council may issue warnings to such enterprise, impose a fine between RMB 1,000,000 and RMB 10,000,000, and, in cases of severe violations, an order to suspend relevant business or halt operation for rectification, revoke relevant business permits or operational licenses, and issue warnings to the controlling shareholders, actual controlling persons, board directors, supervisors, and senior executives of such enterprises, and/or impose a fine between RMB 500,000 and RMB 5,000,000.
In addition, warnings may be issued to relevant securities companies and law firms if they fail to strictly perform their duties or urge the enterprises to comply with the rules, together with a fine between RMB 500,000 and RMB 5,000,000. Personnel in such securities companies or law firms who are responsible are subject to warnings and may be imposed a fine between RMB 200,000 and RMB 2,000,000.
III. Conclusion
With the gradual implementation and improvement of the PRC cybersecurity review legal regime, for enterprises seeking overseas listing, the implementation, assessment and audit of data compliance before the listing and the confirmation of the legal requirement to conduct proactive application of cybersecurity review according to the laws have become a new issue. After heated public debates, a well-known academic journal database company was investigated for a cybersecurity review on June 24, 2022, which shows that the cybersecurity review will be more frequent and stringent in the near future for companies engaging in “network products and services and data processing activities that affect or may affect national security”; this new issue should be given due attention. On the one hand, enterprises shall establish and implement their own tailored and high-standard cybersecurity, data security and personal information protection-related rules in order to achieve internal compliance to the maximum degree; on the other hand, if an enterprise has to initiate a proactive review application or is ordered by the regulatory authorities to initiate the cybersecurity review ex officio, it is advised to deal with the review calmly and actively cooperate with the relevant authorities and carry out the follow-up work. If the cybersecurity review involves a Chinese company seeking to list abroad or overseas, the company must build a comprehensive data compliance system before listing, in order to respond to the inquiries of underwriters/sponsors and intermediary service providers as well as the examination and verification of the regulatory authorities during the listing process. If, after self-assessment, the company believes that a cybersecurity review is required, the company shall perform this obligation before submitting the listing materials so as to comply with the regulatory requirements and avoid compliance risks.
Notes:
[1] http://www.cac.gov.cn/2022-06/24/c_1657686783575480.htm。
[2] http://www.cac.gov.cn/2021-07/02/c_1626811521011934.htm。